### - Ericsson Multiple Stored & Reflected XSS [](https://images.seebug.org/1583429355553-w331s)**_Ericsson RX8200_** devices are vulnerable to multiple reflected and stored XSS **Affected Devices:** - _**RX8200 - Version 5.13.3**_ **XSS Reflected:** Injecting javascript code into the " _path_ " parameter in any of the menus in the URL using GET or POST we get a reflected xss [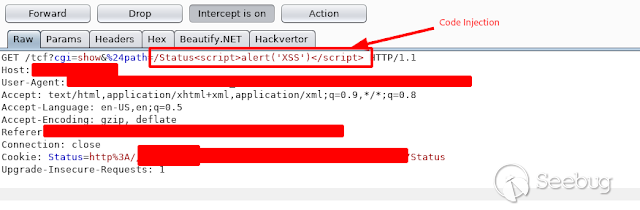](https://images.seebug.org/1583429364605-w331s) [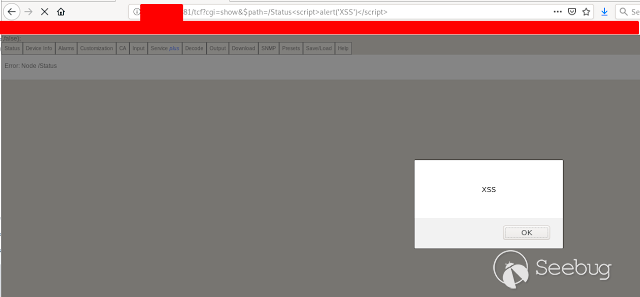](https://images.seebug.org/1583429368598-w331s) [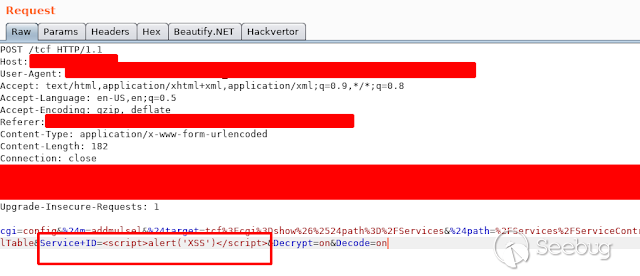](https://images.seebug.org/1583429371805-w331s) [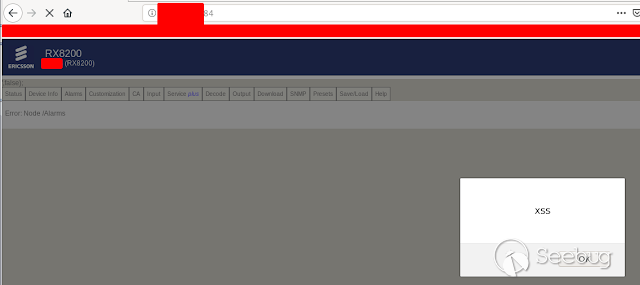](https://images.seebug.org/1583429375374-w331s) We also found another one in the " _Service + ID_ " Parameter [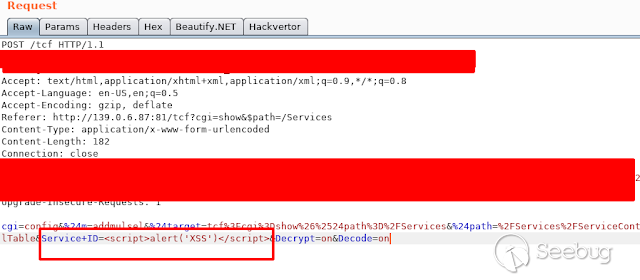](https://images.seebug.org/1583429378361-w331s)...
### - Ericsson Multiple Stored & Reflected XSS [](https://images.seebug.org/1583429355553-w331s)**_Ericsson RX8200_** devices are vulnerable to multiple reflected and stored XSS **Affected Devices:** - _**RX8200 - Version 5.13.3**_ **XSS Reflected:** Injecting javascript code into the " _path_ " parameter in any of the menus in the URL using GET or POST we get a reflected xss [](https://images.seebug.org/1583429364605-w331s) [](https://images.seebug.org/1583429368598-w331s) [](https://images.seebug.org/1583429371805-w331s) [](https://images.seebug.org/1583429375374-w331s) We also found another one in the " _Service + ID_ " Parameter [](https://images.seebug.org/1583429378361-w331s) [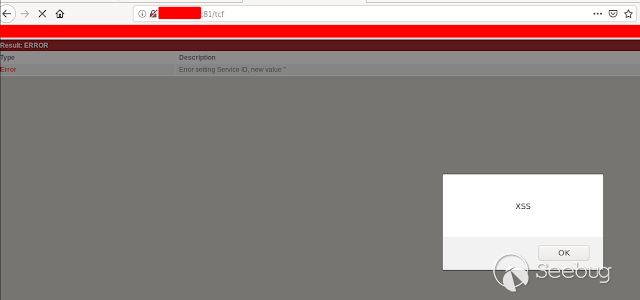](https://images.seebug.org/1583429381956-w331s) **Stored XSS:** Injecting the javascript code in the name of the devices, and then refreshing the page we can see how the XSS sotored is executed [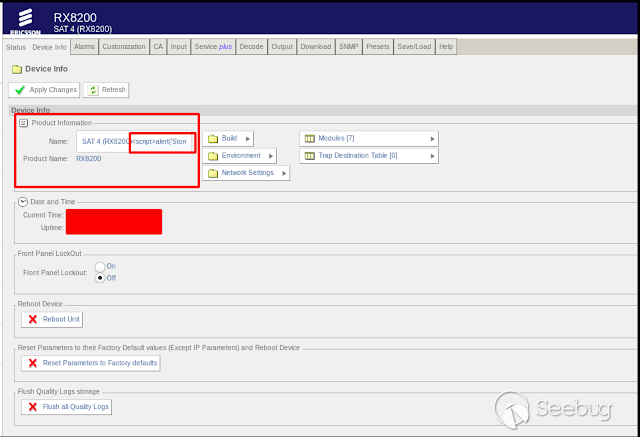](https://images.seebug.org/1583429385002-w331s) [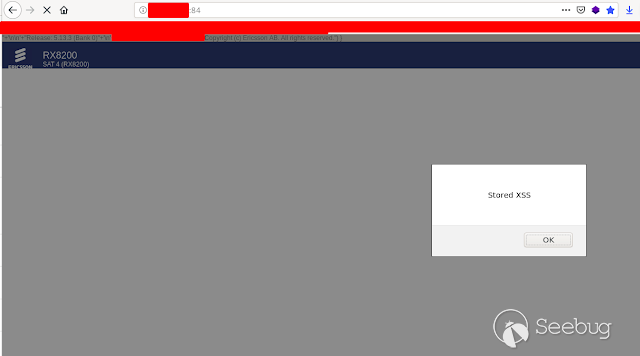](https://images.seebug.org/1583429388679-w331s) By: @Linuxmonr4