### Vulnerability Summary The following advisory describes an information disclosure found in the following TrendNet routers: * TEW-751DR – v1.03B03 * TEW-752DRU – v1.03B01 * TEW733GR – v1.03B01 TRENDnet’s “N600 Dual Band Wireless Router, model TEW-751DR, offers proven concurrent Dual Band 300 Mbps Wireless N networking. Embedded GREENnet technology reduces power consumption by up to 50%. For your convenience this router comes pre-encrypted and features guest networks. Seamlessly stream HD video with this powerful router.” ### Credit An independent security researcher has reported this vulnerability to Beyond Security’s SecuriTeam Secure Disclosure program. ### Vendor response Several attempts to email TrendNet went unanswered, we have no idea what is the status of a fix or availability of a workaround. ### Vulnerability details When an Admin is log-in to one of the mentioned TrendNet routers – it will trigger the global variable: `$AUTHORIZED_GROUP >= 1`. An attacker can use this...
### Vulnerability Summary The following advisory describes an information disclosure found in the following TrendNet routers: * TEW-751DR – v1.03B03 * TEW-752DRU – v1.03B01 * TEW733GR – v1.03B01 TRENDnet’s “N600 Dual Band Wireless Router, model TEW-751DR, offers proven concurrent Dual Band 300 Mbps Wireless N networking. Embedded GREENnet technology reduces power consumption by up to 50%. For your convenience this router comes pre-encrypted and features guest networks. Seamlessly stream HD video with this powerful router.” ### Credit An independent security researcher has reported this vulnerability to Beyond Security’s SecuriTeam Secure Disclosure program. ### Vendor response Several attempts to email TrendNet went unanswered, we have no idea what is the status of a fix or availability of a workaround. ### Vulnerability details When an Admin is log-in to one of the mentioned TrendNet routers – it will trigger the global variable: `$AUTHORIZED_GROUP >= 1`. An attacker can use this global variable to bypass security checks and use it to read arbitrary files. If we will extract the firmware and load it into IDA and take a look at cgibin (phpcgi_main function)- will see that the following: 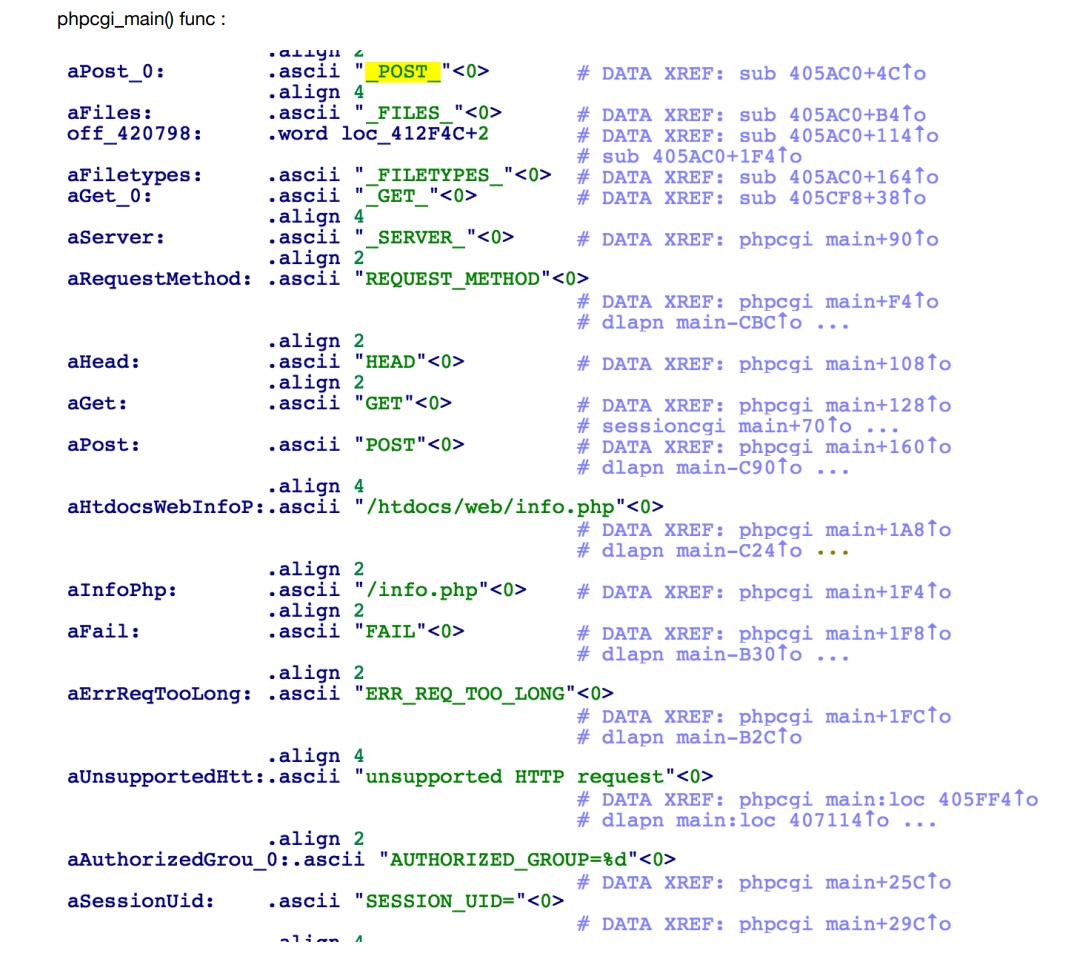 The interesting part here is the REQUEST_METHOD (HEAD, GET, POST) and how it’s parse the request (cgibin_parse_request): 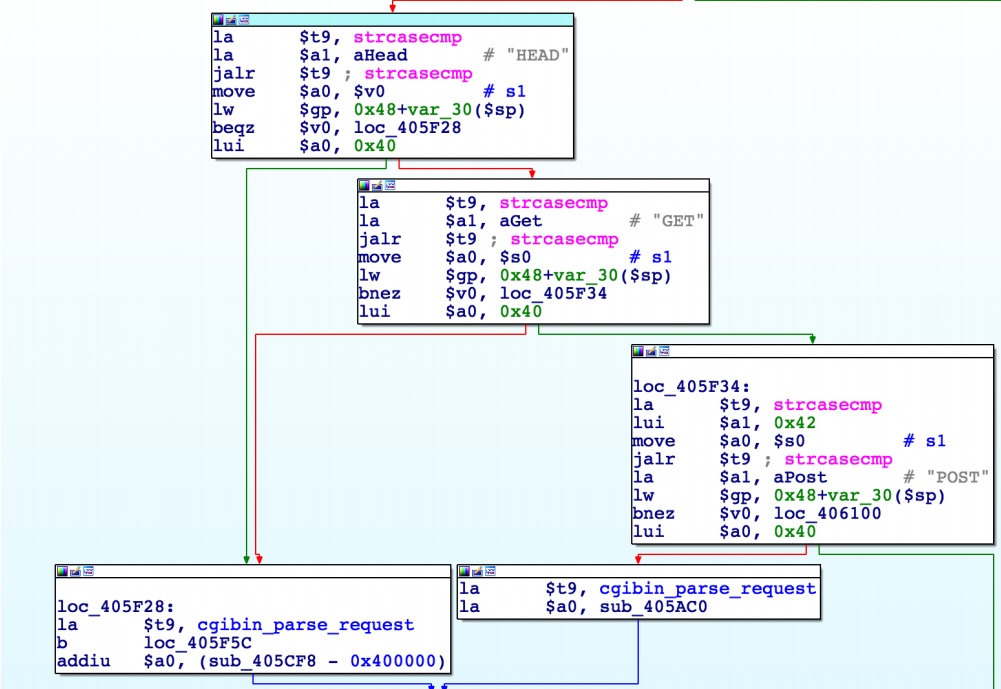 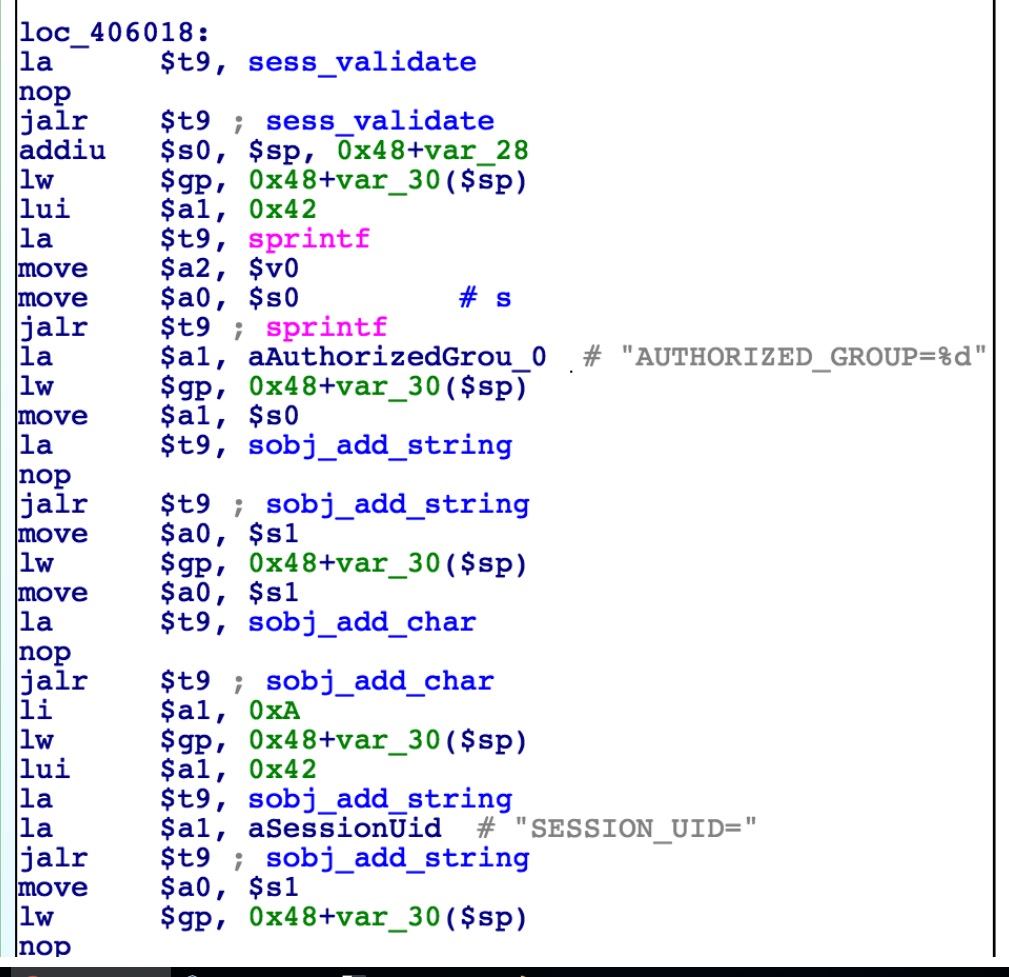 It should look like that: 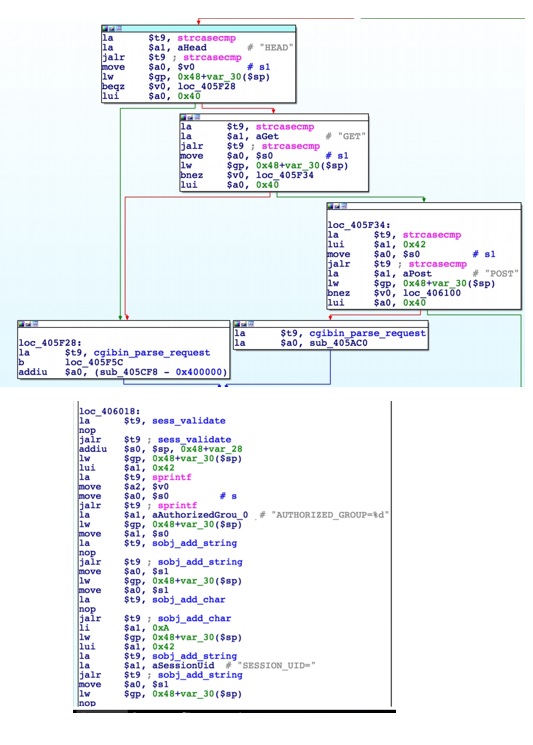 Unauthorized users can not execute statements -> AUTHORIZED_GROUP=-1 But, the functions sub_405CF8() is executed before sess_validate() sub_405CF8() is where you get the AUTHORIZED_GROUP value. 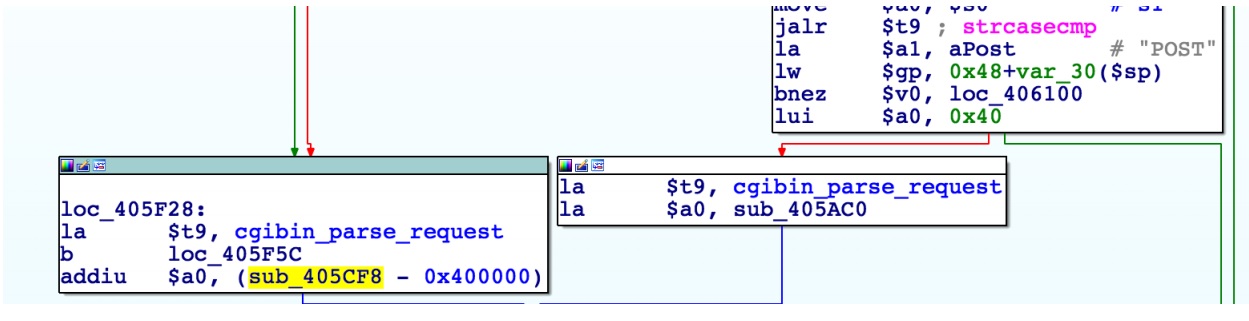 Therefore, If you put AUTHORIZED_GROUP=1 in the request value, you can execute the statement as an authorized user.