
TCcms v9.0...
-
AV
AC
AU
C
I
A
发布:
2025-04-13
修订:
2025-04-13
###0x01漏洞简介 TCcms v9.0 版本在文件/app/controller/user.class.php处的参数userId 存在SQL注入漏洞。 ###0x02漏洞分析 先看文件/app/model/newsAction.class.php,108行开始 ``` public function getCountByUid() { $info = $this->query("select count(*) as total from tc_news where uid=".$_COOKIE["userId"]); return $info[0]["total"]; } } ``` 再看看getCountByUid函数被应用在何处,/app/controller/user.class.php,228行开始 ``` public function home() { $this->userIsLogin (); $newsObj = M ( "news" ); $newsTotal = $newsObj->getCountByUid (); $this->setValue ( "newsTotal", $newsTotal ); $this->forward ( "user/home.html" ); } ``` 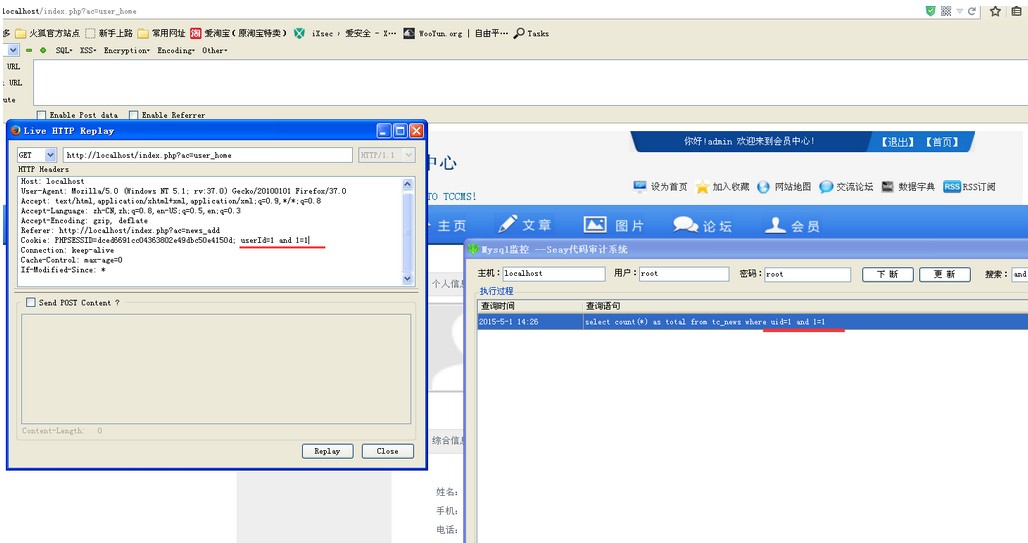 ###0x03修复方案 过滤。
漏洞利用/PoC
暂无可用Exp或PoC
受影响的平台与产品
当前有0条受影响产品信息
