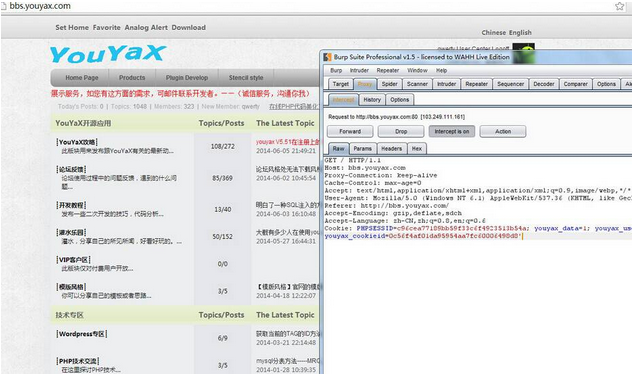
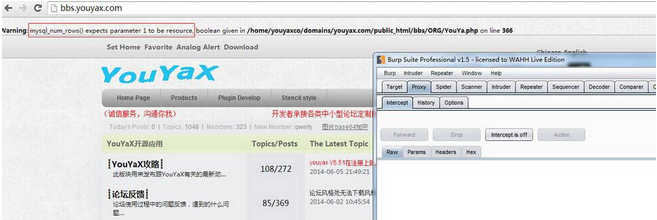
问题出现在ORG/YouYa.php文件中。 第356行: ``` public function find($table, $ext = "string", $param) { //在 param 中寻找与给定的正则表达式 pattern 所匹配的子串 if (preg_match_all("/=/", $param, $tmp)) { $sql = "select * from " . $table . " where " . $param; //echo 'x'.$sql; } else { $param = "id=$param"; $sql = "select * from " . $table . " where " . $param; //echo 'y'.$sql; } $result = mysql_query($sql); $num = mysql_num_rows($result); if ($num <= 0) { return false; } else { $arr = mysql_fetch_array($result); switch ($ext) { case "number": foreach ($arr as $k => $v) { if (is_string($k)) { unset($arr[$k]); } } break; case "string": foreach ($arr as $k => $v) { if (is_numeric($k)) { unset($arr[$k]); } } break; } return $arr; } } ``` 这里对传入的param参数没有进行过滤,导致存在SQL注入危险。 随便找一处调用该函数的地方,文件Lib/ListAction.php,第165行,index方法内 ``` if(isset($_COOKIE['youyax_data']) && isset($_COOKIE['youyax_user']) && isset($_COOKIE['youyax_bz'])){ //echo $_COOKIE['youyax_user']; if($this->find(C('db_prefix') . "user", 'string', "user='" ....
问题出现在ORG/YouYa.php文件中。 第356行: ``` public function find($table, $ext = "string", $param) { //在 param 中寻找与给定的正则表达式 pattern 所匹配的子串 if (preg_match_all("/=/", $param, $tmp)) { $sql = "select * from " . $table . " where " . $param; //echo 'x'.$sql; } else { $param = "id=$param"; $sql = "select * from " . $table . " where " . $param; //echo 'y'.$sql; } $result = mysql_query($sql); $num = mysql_num_rows($result); if ($num <= 0) { return false; } else { $arr = mysql_fetch_array($result); switch ($ext) { case "number": foreach ($arr as $k => $v) { if (is_string($k)) { unset($arr[$k]); } } break; case "string": foreach ($arr as $k => $v) { if (is_numeric($k)) { unset($arr[$k]); } } break; } return $arr; } } ``` 这里对传入的param参数没有进行过滤,导致存在SQL注入危险。 随便找一处调用该函数的地方,文件Lib/ListAction.php,第165行,index方法内 ``` if(isset($_COOKIE['youyax_data']) && isset($_COOKIE['youyax_user']) && isset($_COOKIE['youyax_bz'])){ //echo $_COOKIE['youyax_user']; if($this->find(C('db_prefix') . "user", 'string', "user='" . $_COOKIE['youyax_user'] . "' and cookieid='".$_COOKIE['youyax_cookieid']."'")){ $_SESSION['youyax_data'] = $_COOKIE['youyax_data']; $_SESSION['youyax_user'] = $_COOKIE['youyax_user']; $_SESSION['youyax_bz'] = $_COOKIE['youyax_bz']; } } ``` 这里find函数将用户cookie信息中的youyax_user、cookieid带入到sql中查询,而这两个值用户是可以控制的。cookieid点存在注射问题。 POC: PHPSESSID=c96cea77189bb59f33c6f4923513b54a; youyax_data=1; youyax_user=qwerty; youyax_bz=1; youyax_cookieid=0c56f4af01da95954aa7fc60006498d8' 以官网http://bbs.youyax.com/为例: